Nextelco:VPN setup
From its-wiki.no
VPN
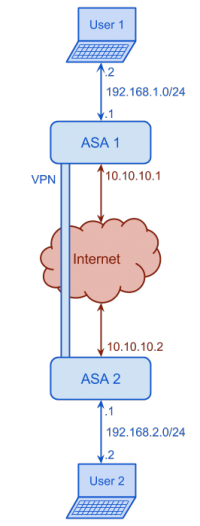
Cisco ASA supports different types of VPNs. In this section Lan2Lan or Site2Site IPsec VPN is explained. We have two ASA 5505 devices and we want to create an IPsec VPN. The following figure shows the network diagram.
In order to set up the VPN we will start with ASA1 configuration. We assume that ASA1 is not configured yet.
- Connect from console port, configure hostname, interfaces, ICMP inspection, NAT and ssh connection.
- Now we can establish ssh connection and configure it through User 1 pc. So let start with some preliminary steps. The first thing will be to create two access-lists in order to identify traffic going from one side to another. The first access-list will be used to identify which traffic ASA has to encrypt and the second to know which traffic does not have to translate.
- So now we will configure the tunnel.
- Firts of all, we will enable isakmp in the outside interface. isakmp (Internet Security Association Key Management Protocol) is the hand-shake part of the configuration.
- Then we set up tunnel's remote ip address and the type of tunnel. In this case Lan2Lan (l2l).
- Establish the tunnel attributes
- The first attribute will be the pre-shared key
- Keepalive time
- After setting the preliminary configuration let continue with tunnel phase 1 (hand-shake [key exchange])
- First we will set that we are going to use pre-shared key
- Next we need to set our encryption
- The hashing algorithm
- Finally the diffie-helman group and the key livetime
- Now is time for phase 2 (setting up the tunnel)
- The first thing is to define the transform set
- Now we have to map the cryptomap to the access control list
- Then we are going to configure perfect forwarding secrecy which randomizes TCP sequence numbers adding another layer of security
- Next we are going to identify our peer, the other end of the connection
- Then we are going to say to our cryptomap which transform set to use
- Finally we are going to apply the cryptomap to the outside interface
- So now we are going to configure NAT in order to specify not to translate this addresses.
- Finally we are going to configure the default route
- Last step, save the configuration
- First of all we create the necessary access-lists.
- So now we will configure the tunnel.
- Firts of all, we will enable isakmp in the outside interface. isakmp (Internet Security Association Key Management Protocol) is the hand-shake part of the configuration.
- Then we set up tunnel's remote ip address and the type of tunnel. In this case Lan2Lan (l2l).
- Establish the tunnel attributes
- The first attribute will be the pre-shared key
- Keepalive time
- After setting the preliminary configuration let continue with tunnel phase 1 (hand-shake [key exchange])
- First we will set that we are going to use pre-shared key
- Next we need to set our encryption
- The hashing algorithm
- Finally the diffie-helman group and the key livetime
- Now is time for phase 2 (setting up the tunnel)
- The first thing is to define the transform set
- Now we have to map the cryptomap to the access control list
- Then we are going to configure perfect forwarding secrecy which randomizes TCP sequence numbers adding another layer of security
- Next we are going to identify our peer, the other end of the connection
- Then we are going to say to our cryptomap which transform set to use
- Finally we are going to apply the cryptomap to the outside interface
- So now we are going to configure NAT in order to specify not to translate this addresses.
- Finally we are going to configure the default route
- Last step, save the configuration
ciscoasa>enable Password: ciscoasa#configure terminal ciscoasa(config)#hostname ASA1 ASA1(config)#interface vlan 1 ASA1(config-if)#ip address 192.168.1.1 255.255.255.0 ASA1(config-if)#nameif inside INFO: Security level for "inside" set to 100 by default. ASA1(config-if)#interface vlan 2 ASA1(config-if)#ip address 10.10.10.1 255.255.255.0 ASA1(config-if)#nameif outside INFO: Security level for "outside" set to 0 by default. ASA1(config-if)#exit ASA1(config)#interface ethernet0/0 ASA1(config-if)#switchport access vlan 2 ASA1(config-if)#no shutdown ASA1(config-if)#exit ASA1(config)#interface ethernet0/1 ASA1(config-if)#no shutdown ASA1(config-if)#exit ASA1(config)#policy-map global_policy ASA1(config-pmap)#class inspection_default ASA1(config-pmap-c)#inspect icmp ASA1(config-pmap-c)#exit ASA1(config-pmap)#exit ASA1(config)#access-list inside_nat_outside extended permit ip 192.168.1.0 255.255.255.0 10.10.10.0 255.255.255.0 ASA1(config)#nat (inside) 1 access-list inside_nat_outside ASA1(config)#global (outside) 1 interface ASA1(config)#username basicinternet password basicinternet privilege 15 ASA1(config)#crypto key generate rsa modulus 2048 WARNING: You have a RSA keypair already defined name <Default-RSA-Key>. Do you really want to replace them? [yes/no]: yes Keypair generation process begin. Please wait... ASA1(config)#aaa authentication ssh console LOCAL ASA1(config)#ssh 192.168.1.0 255.255.255.0 inside ASA1(config)#write memory ASA1(config)#exit ASA1#exit ASA1>
terminal$ ssh basicinternet@192.168.1.1 basicinternet@192.168.1.1's password: ASA1>enable Password: ASA1#configure terminal ASA1(config)#access-list lan_to_lan permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0 ASA1(config)#access-list nat0_lan_to_lan permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
ASA1(config)#crypto isakmp enable outside
ASA1(config)#tunnel-group 10.10.10.2 type ipsec-l2l
ASA1(config)#tunnel-group 10.10.10.2 ipsec-attributes
ASA1(config-tunnel-ipsec)#pre-shared-key basicinternet
ASA1(config-tunnel-ipsec)#isakmp keepalive threshold 10 retry 2 ASA1(config-tunnel-ipsec)#exit
ASA1(config)#crypto isakmp policy 10 authentication pre-share
ASA1(config)#crypto isakmp policy 10 encrypt 3des
ASA1(config)#crypto isakmp policy 10 hash sha
ASA1(config)#crypto isakmp policy 10 group 2 ASA1(config)#crypto isakmp policy 10 lifetime 86400
ASA1(config)#crypto ipsec transform-set ESP-3DES-SHA esp-des esp-sha-hmac
ASA1(config)#crypto map map_lan_to_lan 1 match address lan_to_lan
ASA1(config)#crypto map map_lan_to_lan 1 set pfs group1
ASA1(config)#crypto map map_lan_to_lan 1 set peer 10.10.10.2
ASA1(config)#crypto map map_lan_to_lan 1 set transform-set ESP-3DES-SHA
ASA1(config)#crypto map map_lan_to_lan interface outside
ASA1(config)#nat (inside) 0 access-list nat0_lan_to_lan
ASA1(config)#route outside 192.168.2.0 255.255.255.0 10.10.10.2
ASA1(config)#write memory Building configuration... Cryptochecksum: c47ca90d a167f297 2fb5ca80 2d4343fe 3929 bytes copied in 1.740 secs (3929 bytes/sec) [OK] ASA1(config)#
So lets continue with ASA2 configuration. We assume that ASA2 has been already configured and that we are connected through ssh.
ASA2(config)#access-list lan_to_lan permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0 ASA2(config)#access-list nat0_lan_to_lan permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0
ASA2(config)#crypto isakmp enable outside
ASA2(config)#tunnel-group 10.10.10.1 type ipsec-l2l
ASA2(config)#tunnel-group 10.10.10.1 ipsec-attributes
ASA2(config-tunnel-ipsec)#pre-shared-key basicinternet
ASA2(config-tunnel-ipsec)#isakmp keepalive threshold 10 retry 2 ASA2(config-tunnel-ipsec)#exit
ASA2(config)#crypto isakmp policy 10 authentication pre-share
ASA2(config)#crypto isakmp policy 10 encrypt 3des
ASA2(config)#crypto isakmp policy 10 hash sha
ASA2(config)#crypto isakmp policy 10 group 2 ASA2(config)#crypto isakmp policy 10 lifetime 86400
ASA2(config)#crypto ipsec transform-set ESP-3DES-SHA esp-des esp-sha-hmac
ASA2(config)#crypto map map_lan_to_lan 1 match address lan_to_lan
ASA2(config)#crypto map map_lan_to_lan 1 set pfs group1
ASA2(config)#crypto map map_lan_to_lan 1 set peer 10.10.10.1
ASA2(config)#crypto map map_lan_to_lan 1 set transform-set ESP-3DES-SHA
ASA2(config)#crypto map map_lan_to_lan interface outside
ASA2(config)#nat (inside) 0 access-list nat0_lan_to_lan
ASA2(config)#route outside 192.168.1.0 255.255.255.0 10.10.10.1
ASA2(config)#write memory Building configuration... Cryptochecksum: c47ca90d a167f297 2fb5ca80 2d4343fe 3929 bytes copied in 1.740 secs (3929 bytes/sec) [OK] ASA2(config)#
These are all the steps, now we should be able to ping User 2 computer from User 1 computer, as well as to connect to User 2 node web page.