Nextelco:CNOC Norway
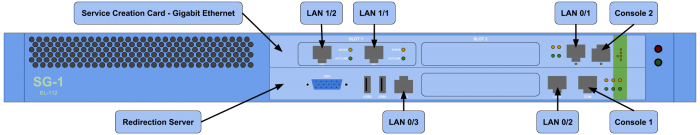
The Runcom CNOC available in Norway is composed by two components, each one installed in a different front slot.
- In the first slot there is the SCC-GEth (Service Creation Card - Gigabit Ethernet) module.
- In the second slot there is the RDS (Redirection Server) module.
The following figure shows how is the CNOC physically.
Getting access
As it is shown in the previous figure, both components or modules, have several ethernet connections as well as a console ports. Console ports are intended to be the first way of getting access, which requires local presence, however none of the components is answering by this port.
The default configuration allows to get access through console ports, however, these CNOC has been already manipulated and that is why console ports are not responding.
The second option to get access is using ethernet ports and by telnet or ssh. For that purpose is necessary to now which is the IP address of the port. Since CNOC was already configured that is not an straight forward action. To solve that issue there are two possible solutions:
- With a tool such as NMAP (Network exploration tool), which can be used to analyze all possible IP addresses and try to find to which ones does the CNOC answer
- If the CNOC provides an IP address, try to use Wireshark (Packet analyzer tool) to figure out which is the IP address of the DHCP server.
During the first access the second option was used. That solution provide us the IP address of the DHCP server, which in this case is 192.168.0.3. Unfortunately, not telnet neither ssh were able to get access.
After scanning several IP ranges and trying both telnet and ssh, finally we got access.
- To connect to the first module, the SCC-GEth, it is necessary to connect to the LAN 1/1 port and use telnet to 192.168.11.3 IP address. Then we need the default credentials to get access.
telnet 192.168.11.3
- To connect to the second module, the RDS, it is necessary to connect to the LAN 0/3 port and use ssh to 192.168.11.4 IP address.
ssh te@192.168.11.4
Hardware & Software specifications
These are hardware and software specifications of the SCC module:
CNOC> show version hardware Module Num Part No. Serial No. Slot --------- --- ---------------- ---------- ---- Backplane 1 710-200-0 Rev 0 0 SCC-GEth 2 650-045 Rev 2 906771 1
CNOC> show version software Module Num Application -------- --- ------------------------- SCC-GEth 1 13.0 Dec 11 2012 16:45:56
CNOC> show version pack Pack Image Name: V130_7055_PM Version: V13.0 December 11 2012 17:19:28 Size: 1951170 byte Pack Components: Main Image Version: 13.0 Dec 11 2012 16:45:56 Main Description: Service Creation File GOS.ini Image Version: V13.0 File Description: INI for GOS File V130.mib.zip Image Version: version File Description: SCC MIB
These are hardware and software specifications of the RDS module:
RDSHost> show version hardware Module Num Part No. Serial No. Version ------ --- -------- ---------- ---------------- RDS 1 780-002 D0C9BA9DE8 V2.0_RDS_1866.717
RDSHost> show version software Module Num Version ------ --- ------------- RDS 1 V4.1.10.0_RDS Kernel 2 2.4.32
RDSHost> show version pack Pack Image Name: RDS_4_1_10 Version: V4.1.10.0_RDS_pack Size: 0 Pack Components: Kernel Version: 2.4.32 EDS Version: V4.1.10.0_RDS
Predefined Configuration
The CNOC came with the following configuration:
RDSHost> write terminal #version V4.1.10.0_RDS 2014/08/13 16:42:41 password operator gfwhs^k password technician jep^us default-redirection-site http://91.207.159.21:8657/nextt/web_authentication.html hostname RDSHost interface ethernet 1 192.168.11.4 255.255.255.0 ip default-gw 192.168.11.1 error-level 0 output-device console event-level 0 output-device console sysLog-server-ip 0.0.0.0 remote-ip-in-ip 192.168.11.3 snmp-server community set public snmp-server community get public access-list snmp-permit 0.0.0.0 0.0.0.0
RDSHost> show route RDS IP routing table Destination Gateway Mask 192.168.11.0 0.0.0.0 255.255.255.0 192.168.11.0 0.0.0.0 255.255.255.0 127.0.0.0 0.0.0.0 255.0.0.0 0.0.0.0 192.168.11.1 0.0.0.0
RDSHost> show certificate Certificate: Data: Version: 3 (0x2) Serial Number: 0 (0x0) Signature Algorithm: md5WithRSAEncryption Issuer: C=IL, ST=Herzeliya, L=Herzeliya, O=ADC, OU=ADC-UNIT, CN=www.sg1-rds.com/Email=raviv.zeev@g-connect.co.il Validity Not Before: Mar 27 11:07:03 2007 GMT Not After : May 5 11:07:03 2011 GMT Subject: C=IL, ST=Herzeliya, L=Herzeliya, O=ADC, OU=ADC-UNIT, CN=www.sg1-rds.com/Email=raviv.zeev@g-connect.co.il Subject Public Key Info: Public Key Algorithm: rsaEncryption RSA Public Key: (1024 bit) Modulus (1024 bit): 00:c7:68:2d:73:5e:8b:03:3a:86:21:6a:74:21:67: ec:ab:32:f3:9c:69:8b:63:16:74:76:37:0f:fb:e1: 19:82:bf:56:7f:ca:7d:5a:fe:38:ba:db:91:31:35: 25:14:b5:be:d1:b3:2f:b1:0d:6f:06:65:29:bf:8a: 9e:e2:6b:12:73:71:bf:0b:10:24:c3:da:1f:c5:11: df:7f:78:8c:ff:a2:54:9e:f8:a5:e0:51:a1:81:44: 62:79:e4:9c:b3:49:1f:79:5c:0f:97:6f:de:57:66: 33:92:8e:57:a0:af:37:7f:c4:94:88:11:f7:2c:3e: c4:a3:4d:a6:11:61:27:b8:c7 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: B8:22:3A:CC:14:40:CB:1C:66:10:79:20:44:15:83:29:81:65:20:FE X509v3 Authority Key Identifier: keyid:B8:22:3A:CC:14:40:CB:1C:66:10:79:20:44:15:83:29:81:65:20:FE DirName:/C=IL/ST=Herzeliya/L=Herzeliya/O=ADC/OU=ADC-UNIT/CN=www.sg1-rds.com/Email=raviv.zeev@g-connect.co.il serial:00 X509v3 Basic Constraints: CA:TRUE Signature Algorithm: md5WithRSAEncryption ae:96:ef:cd:e3:a1:a1:c9:c6:75:d3:50:c2:8b:08:b1:39:ae: 4a:15:26:52:ec:ab:63:9f:ee:21:72:47:13:24:0f:cd:da:bb: 31:7f:7f:7a:1d:d1:0d:5d:f2:19:b3:ef:cc:7c:67:80:4b:a1: 99:68:cc:4d:7e:62:07:c0:7b:91:f6:0f:b4:bb:d3:c7:4f:ae: d2:4b:f7:51:ec:0c:2d:52:b0:6d:33:f7:d7:62:d6:1f:b4:e0: ef:fe:4d:2d:b7:a7:95:14:b8:29:2e:de:eb:4e:ef:d3:bb:af: 6a:25:6f:96:a3:05:15:72:0f:60:57:45:1a:d7:31:e7:9a:e0: d0:e2
Redirection Server
The Redirection Server is an FCS’s product that redirects all peers’ Http requests to their personal-sites as pre-defined in the Radius server. The RDS uses FCS’s EDS (Enhanced Dynamic Services) policy to redirect the connected peers and it actually acts as a sophisticated SSC (Service Creation Card).
The RDS is usually located at the ISP/Carrier network but it is not mandatory. When the RDS is located outside the access subnet the ASN-SG (Access Service Network - Service Gateway) uses an IP in IP tunnel to transfer the redirected data.
Return to Technology page.