Nextelco:ASA nat
ASA NAT
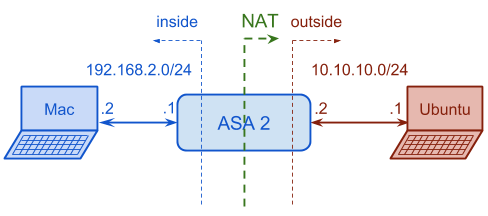
In this section we will set up NAT in order to translate all IP headers of the packets going from inside to outside interfaces. At the same time the ASA will translate the packets coming back from the outside interface. We assume that ASA has already VLANs, IPs, interfaces, and ICMP traffic inspection configured from previous step.
- The first step is to configure an access-list which will identify all IP traffic going from inside 192.168.2.0/24 network to outside 10.10.10.0/24 network.
- After configuring the access-list it is necessary to create a nat rule for the inside interface, which will be the one that will be translated.
- And finally, a global rule has to be created for the outside interface in order to activate PAT and be able to translate all inside to outside communications using different port numbers.
ASA2(config)#access-list inside_nat_outside extended permit ip 192.168.2.0 255.255.255.0 10.10.10.0 255.255.255.0
ASA2(config)#nat (inside) 1 access-list inside_nat_outside
ASA2(config)#global (outside) 1 interface INFO: outside interface address added to PAT pool
With the previous configuration, the ASA was not translating the IP addresses of inside host, Mac, so the outside host, Ubuntu, was able to see that the internal 192.168.2.2 address was sending the ping messages. In the same way Ubuntu host need to know that in order to reach the net 192.168.2.0/24, it should send the packet to 10.10.10.2 IP address.
Now, with NAT enabled, Ubuntu sees packets coming from 10.10.10.2 instead of 192.168.2.2, so it doesn't know anything about which IP addresses are used in the internal side and it doesn't need to know that in order to reach that network it should send the packets to 10.10.10.2.
Return to Phase 1 page.