Nextelco:VPN setup
From its-wiki.no
VPN
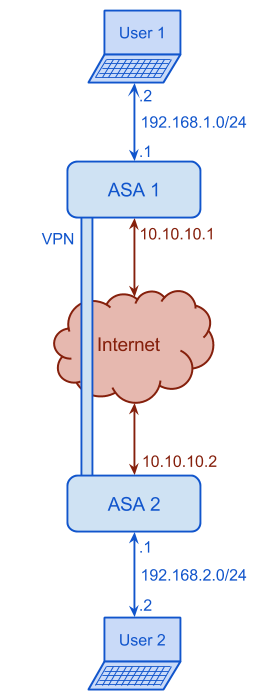
Cisco ASA supports different types of VPNs. In this section Lan2Lan or Site2Site IPsec VPN is explained. We have two ASA 5505 devices and we want to create an IPsec VPN. The following figure shows the network diagram.
In order to set up the VPN we will start with ASA1 configuration. We assume that ASA is not configured yet.
- Connect from console port, configure hostname, interfaces and ssh connection.
ciscoasa>enable Password: ciscoasa#configure terminal ciscoasa(config)#hostname ASA1 ASA1(config)#interface vlan 1 ASA1(config-if)#ip address 192.168.1.1 255.255.255.0 ASA1(config-if)#nameif inside INFO: Security level for "inside" set to 100 by default. ASA1(config-if)#interface vlan 2 ASA1(config-if)#ip address 10.10.10.1 255.255.255.0 ASA1(config-if)#nameif outside INFO: Security level for "inside" set to 0 by default. ASA1(config-if)#exit ASA1(config)#interface ethernet0/0 ASA1(config-if)#switchport access vlan 2 ASA1(config-if)#no shutdown ASA1(config-if)#exit ASA1(config)#interface ethernet0/1 ASA1(config-if)#no shutdown ASA1(config-if)#exit ASA1(config)#username basicinternet password basicinternet privilege 15 ASA1(config)#crypto key generate rsa modulus 2048 WARNING: You have a RSA keypair already defined name <Default-RSA-Key>. Do you really want to replace them? [yes/no]: yes Keypair generation process begin. Please wait... ASA1(config)#aaa authentication ssh console LOCAL ASA1(config)#ssh 192.168.1.0 255.255.255.0 inside ASA1(config)#write memory ASA1(config)#exit ASA1#exit ASA1>