Difference between revisions of "Master: Device connectivity through InfoInternet"
From its-wiki.no
Josef.Noll (Talk | contribs) (Created page with "{{Meeting |Title=Master: Device connectivity through InfoInternet |Place=UNIK |Date=2016/12/07 |Duration=1000-1200 |Organiser=Josef.Noll |User=Josef.Noll, Nusrat Nur Syead,...") |
Josef.Noll (Talk | contribs) |
||
| Line 5: | Line 5: | ||
|Duration=1000-1200 | |Duration=1000-1200 | ||
|Organiser=Josef.Noll | |Organiser=Josef.Noll | ||
| − | |User=Josef.Noll | + | |User=Josef.Noll, Syead Nusrat Nur, |
}} | }} | ||
| − | + | = Discussion on Master Thesis = | |
| + | based on [[Integrating_Energy_Devices_through_BasicInternet]] | ||
| + | |||
| + | 1) Scenario connecting the washing machine | ||
| + | |||
| + | [[Filet:201612Washing.png]] | ||
| + | |||
| + | 2) Security analysis of [[InfoInternet]] | ||
| + | * free access to Information through e.g. the Opera Mini Proxy | ||
| + | * advantages and challenges from a security point of view | ||
| + | |||
| + | |||
| + | |||
| + | |||
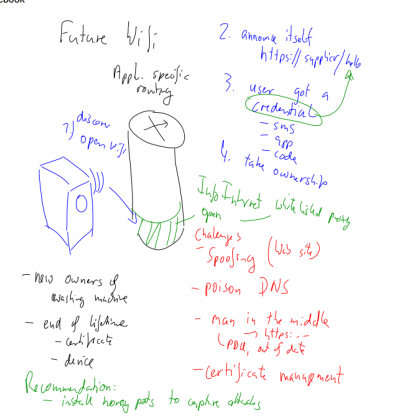
| + | 3) security analysis of the washing machine scenario | ||
| + | |||
| + | [[File:SecurityAnalysis_Washing.png|400px|Security Analysis Washing machine]] | ||
| + | |||
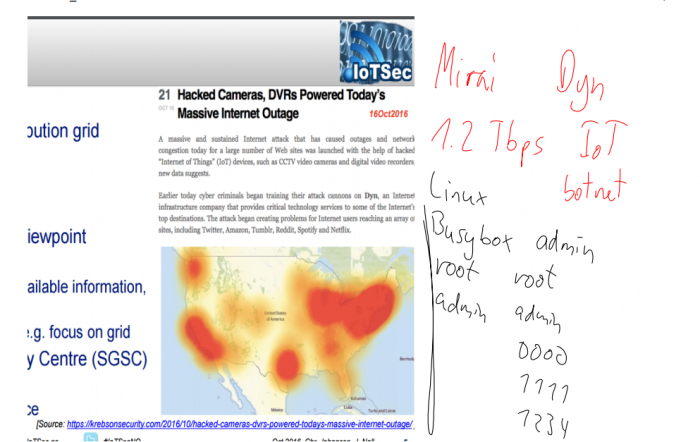
| + | compare to Mirai attack | ||
| + | |||
| + | [[File:Mirai-attack-analysis.png|700px|Mirai attack security analysis]] | ||
| + | 4) if time permits: apply the Multi Metrics Method for measurable security on 3) | ||
Revision as of 10:01, 7 December 2016
| Wiki for ITS | ||||||
|---|---|---|---|---|---|---|
|
Master: Device connectivity through InfoInternet
| Title | Master: Device connectivity through InfoInternet |
|---|---|
| Place | UNIK |
| Date, Time | 2016/12/07, 1000-1200 |
| Contact Person | Josef.Noll |
| Participants | Josef.Noll, Syead Nusrat Nur |
| related to Project | |
| Keywords |
| this page was created by Special:FormEdit/Meeting, and can be edited by Special:FormEdit/Meeting/Master: Device connectivity through InfoInternet |
| Category:Meeting |
Discussion on Master Thesis
based on Integrating_Energy_Devices_through_BasicInternet
1) Scenario connecting the washing machine
2) Security analysis of InfoInternet
- free access to Information through e.g. the Opera Mini Proxy
- advantages and challenges from a security point of view
3) security analysis of the washing machine scenario
compare to Mirai attack
 4) if time permits: apply the Multi Metrics Method for measurable security on 3)
4) if time permits: apply the Multi Metrics Method for measurable security on 3)