SCOTT:Home
From its-wiki.no
| Home | ||||||
|---|---|---|---|---|---|---|
|

Secure Connected Trustable Things (SCOTT) finished in Sep2020
JU ECSEL project SCOTT- Norwegian contribution
SCOTT Project Web page: http://scott-project.eu
Objective of SCOTT
Creating trust in wireless solutions and increasing their social acceptance are major challenges to achieve the full potential of the Internet of Things (IoT). Therefore, SCOTT – Secure COnnected Trustable Things, a pan-European effort with 57 key partners from 12 countries (EU and Brazil), will provide comprehensive cost-efficient solutions of wireless, end-to-end secure, trustworthy connectivity and interoperability (Technology Readiness Level 6-7) to bridge the last mile to market implementation. SCOTT will not just deal with 'things that are connected', but with 'trustable things that securely communicate', i.e. things interconnected by dependable wireless technology and valuing the end-users' privacy rules.
SCOTT will focus on wireless sensor and actuator networks and communication in the areas of mobility, building & home / smart infrastructure as well as health. This addresses numerous European societal challenges such as smart, green and integrated transport, secure and inclusive societies as well as health and wellbeing. SCOTT will enable efficient, trustworthy connectivity and facilitate ubiquity of intelligent embedded systems and systems of systems, thus essentially contributing to burning issues in Automated Vehicles, Industry 4.0, et. See details of the SCOTT objectives at SCOTT: TL Objectives.
Read more at the SCOTT Web: SCOTT-Project.eu
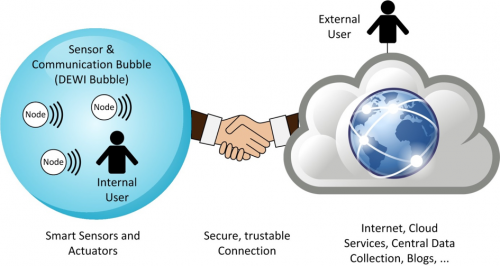
SCOTT uses a standardized multi-domain reference architecture, created in a predecessor project (DEWI and its “Bubble concept”) and being fully compliant with ISO 29182 - Sensor Network Reference Architecture, which fosters reusability, scalability, and interoperability of SCOTT solutions. SCOTT also utilizes a clearly use-case driven approach with 15 use cases from different areas of high relevance to European society and industry; a specific focus will be put on cross-domain use cases and heterogeneous environments, emphasizing 5G and cloud computing aspects to build up digital ecosystems to achieve a broader market penetration.
Facts
- 3 years project, financed in part by JU ECSEL and NFR, EU-Commission Contract 737422
- 57 partners from 12 countries
- total budget of 39.7 M€, with EU support of 10.5 M€ and national support of 12.5 M€
- see more at SCOTT Factpage
Norwegian contribution to SCOTT
| |

|

|

|

|

|

|

|
From Norway 8 partners participate:
- Eye Networks with their EyeSaaS Cloud, focussing on managed Wifi for trustable services;
- OsloMet with their expertise on networking, security, and IoT and the 5G network lab;
- Movation with their innovation ecosystem, focussing on technology outview and start-up opportunities;
- NCE Smart, represented by Smart Innovation Østfold, focussing on applicability for the Norwegian Smart Grid Security Centre
- Telenor with their mobile network connecting the distributed cloud and focus on adaptable network slicing for secure and trusted IoT communications
- TellU with TelluCloud, their technology platform for data gathering, processing and presentation, focussing on applicability in domains of assisted living, e-health and personnel safety;
- UiO with their methodologies for measurable security and privacy, focussing on privacy labelling and quantifiable security for IoT systems;
- Wolffia with their industrial messaging system, focussing one security in adaptable networks.
Read more at SCOTT - Norwegian Participation
Highlights of Results
Videos representing the work
The Norwegian partners recorded several videos demonstrating the different works. Some of these are available through the SCOTT playlist of the CPS Lab channel on YouTube.
Highlights in Short
Privacy Labeling - UiO
For people concerned about privacy when choosing an IoT product, Privacy Labels make it easy to do truly well informed choices. Privacy Labels look like nutrition facts labels when factual details are being presented and look like energy consumption labels when only comparing based on graded scales. Privacy Labels promote 'Privacy as an added value/feature' allowing to differentiate from market competitors. Privacy Labels are legally binding, tied to privacy agreements, so that it cannot become a means of deceit. AI and Natural Language Processing techniques are used to automatically translate between privacy agreements and privacy labels. We are working with bodies like EuroPriSe (from Germany) to enhance GDPR certifications with measurable and usable privacy, going beyond the yes/no compliance. We are working with PrivacyLabels.org (from Netherlands) who provide to privacy conscious companies a way to create privacy labels through a self-evaluation process guided by a web service. Stakeholders include Lay people, Law firms, Regulatory or Certification bodies, and Businesses.
See the video: [1]
Security Classification for DevSecOps - UiO
UiO has developed a security classification method for IoT systems to help and guide developers into building their systems secure from the start. At the same time we wanted to have a way for decision makers to be able to quickly evaluate and compare systems based on their security, hence the concept of a security class. The Security Classification methodology is a way to measure security, building on the standard from the French national agency ANSSI. The methodology moves away from a classical attack-centric approach, into an approach focusing on connectivity (like what ports are opened) and security protection mechanisms (like what encryption do we use).
UiO has built a tool and tested it with end-user to be easy-to-use in a standard DevSecOps tool-chain. This final tool, implementing the security classification methodology, is available as a cloud service to everyone at the link https://LightSC.azurewebsites.net
UiO has applied the security classification to the work packages 21, 9 and 7, also inside the University of Oslo in a course on IoT security, and also in a hackaton contest with a cluster of SMEs from Poland, which Gdansk University helped us to organize.
Semantic Attribute Based Access Control (S-ABAC) - UiO
UiO has worked on combining Attribute Based Access Control with semantic technologies, which UiO called semantic attribute based access control (S-ABAC). We are backward compatible with the XACML standard (extensible access control markup language) as describe by NIST, and widely used in healthcare systems especially in US. The final S-ABAC engine is accessible as a cloud service, deployed in cloud infrastructure of the University of Oslo. The architecture of our engine is closely extendind the XACML architecture. UiO has mainly worked with Work Packages 9 and 21 during our development, and provided two stand-alone demonstrators of S-ABAC for these two pilots. These videos can be found on the above CPS Lab YouTube channel. UiO has collaborated on research with Chalmers University from Sweden and with Luxembourg University.
Diabetes App - Tellu
Tellu as a provider of services in the e-health domain, has developed a diabetes monitoring sub-system, with mobile app serving as a gateway between medical measurement devices and cloud systems. When a patient with diabetes use insulin, the level of glucose may decrease (hypoglycaemia) which can affect on the physical and mental performance and in serious cases it can results in losing consciousness. In this situation care givers need to be alerted and be able to enter o the patient´s house. Tellu in collaborating with Prediktor Medical company provide a prototype device that can be worn as a patch on the skin which does continuously glucose monitoring called BioMKR. BioMKR does a new type of non-intrusive glucose measuring which means it does not been injected to the body and does not connected directly with blood. The device is connected via Bolthouse to a phone app which is called Tellu medical gateway app. This app works as a gateway to connect various medical measurement devices to cloud services. The gateway app also does some local processing of measurements and alerts the relevant system to notify the care giver.
See the video: [6]
Managed Wireless - EyeNetworks
EyeNetworks as the mesh managed wireless market leader is providing total solutions for access networks to Internet service providers. Existing wireless networks perform best-effort data delivery and fail to ensure quality, security and trustability of services. In SCOTT project, EyeNetworks presented a managed wireless concept in order to improve performance, security and trustability of wireless networks and services in smart infrastructure. The managed wireless platform as a cloud service being able to monitor and manage Wi-Fi access points and Internet gateways in homes and buildings remotely. In effect, Internet service providers and third-party service providers can use this platform to monitor quality of service (QoS) and manage their devices or services to perform proactive measures for improving user satisfaction while reducing their operational costs. Furthermore, the managed wireless concept can accelerate user readiness for novel services that require carrier-grade quality in smart infrastructure.
See the video: [7]
5G4IoT - Telenor-OsloMet-Wollfia
Telenor-OsloMet-Wollfia are able to enhance the smart home experience by providing network slicing in 5G networks. For instance, in the smart home for elderly people they have a fall detection system, a smart lock in the main door and a gateway to allow these devices to connect to the cellular network. Besides the smart home slice, there is a health care centre slice that all caregivers are connected to and are able to receive messages in case of any alert detection. The available caregiver who accept the message reach the house and is able to unlock the door by using a QR code and confirmation from the healthcare centre. An identity provider and management system has been added to the network infrastructure to verify the caregivers identity and eligibility to perform a task. This system is responsible to issue and manage all identities for every devices connected to the network. In order to provide network slicing they have succeeded in deploying one of the smallest 5G networks, using off the shelf and consumer available products and open-sourced software, which is located in their Secure 5G4IoT test lab.
See the video:
More information and contacts
Please feel free to contact the project partners
- Josef Noll, Maunya Doroudi Moghadam,Christian Johansen - University of Oslo,
- Linda Firveld, Maghsoud Morshedi, Geir Arne Rimala - Eyenetworks
- Boning Feng - OsloMet
- Toktam Ramezani - University of Oslo
- Bjarne Haugen - Movation
- Heidi Tuiskula - Smart Innovation Norway
- Do van Thanh - Telenor
- Knut Eilif Husa - TellU
- Do van Thuan, -Wolffia
Or follow us on LinkedIn: https://www.linkedin.com/groups/12072936/ and Twitter: https://twitter.com/SCOTTProject2