Difference between revisions of "TEK5530"
From its-wiki.no
Josef.Noll (Talk | contribs) |
Josef.Noll (Talk | contribs) (→Topics) |
||
| Line 27: | Line 27: | ||
=Topics = | =Topics = | ||
| − | The course has the following | + | The course has the following lectures |
| + | * L1: Introduction | ||
| + | * L2: Internet of Things | ||
| + | * L3: Security of IoT | ||
| + | * L4: Smart Grid, Automatic Meter Readings (AMR) | ||
| + | * L5: Service implications on functional requirements | ||
| + | * L6: Technology mapping | ||
| + | * L7: Paper analysis with 15-20 min presentation | ||
| + | * L8: Practical implementation of ontologies | ||
| + | * L9: Logical binding - industrial example | ||
| + | * L10: Multi-Metrics Method for measurable Security | ||
| + | * L11: Multi-Metrics Weighting of an AMR sub-system | ||
| + | * L12: System Security and Privacy analysis | ||
| + | * L13: Phenomena "intrusion-detection" | ||
| + | * L14, L15: Real world examples | ||
| + | |||
== Introduction into Internet of Things (IoT) == | == Introduction into Internet of Things (IoT) == | ||
This first part will provide the introduction into the Internet of Things, with industrial examples | This first part will provide the introduction into the Internet of Things, with industrial examples | ||
Revision as of 14:03, 5 January 2016
| Wiki for ITS | ||||||
|---|---|---|---|---|---|---|
|
TEK5530 - Measurable Security for the Internet of Things
| TEK5530 | |
|---|---|
| News | Lectures on Fridays 0900-1200h, starting from 23Jan2016. The course is given at UNIK (Room 308b), with video communication to Room Scheme@Ifi.UiO.no (1251) |
| Organisation | UNIK |
| by | Josef Noll, György Kálmán |
| Keywords |
|---|
| Abstract | The course provides a methodology for measurable security, privacy, and dependability of industrial systems. Based on e.g. a smart grid example we will establish and develop the methodology to perform a multi-metrics analysis from components to sub-systems to systems. The course will allow you to compare security-related application goals with the results from the system analysis. |
|---|---|
| Objective (max 350 words) | After completing the course you will be able to:
|
| Keywords | Security, Network Security, Sensor Security, Sensor networks |
| Research Area(s) | Security |
| Type of course | Master |
Upload TEK5530.png to see a course picture instead of the banner picture. Edit the page by Special:FormEdit/Course/TEK5530.
To add new lectures, use: Add a lecture
Info
- This course is a Master course.
- The course takes place on Fridays, 0900-1200h at UNIK. A video communication is available to Ifi, Room Scheme@Ifi.UiO.no (room 1251), see check: Video_conference
- We'll have video streaming: mms://lux.unik.no/308
- Evaluation is based on a presentation of topics and the implementation of your scenario.
Topics
The course has the following lectures
- L1: Introduction
- L2: Internet of Things
- L3: Security of IoT
- L4: Smart Grid, Automatic Meter Readings (AMR)
- L5: Service implications on functional requirements
- L6: Technology mapping
- L7: Paper analysis with 15-20 min presentation
- L8: Practical implementation of ontologies
- L9: Logical binding - industrial example
- L10: Multi-Metrics Method for measurable Security
- L11: Multi-Metrics Weighting of an AMR sub-system
- L12: System Security and Privacy analysis
- L13: Phenomena "intrusion-detection"
- L14, L15: Real world examples
Introduction into Internet of Things (IoT)
This first part will provide the introduction into the Internet of Things, with industrial examples
- Smart Grid and automatic meter readings
- Smart Homes with sensors
- Wireless System upgrade of cars
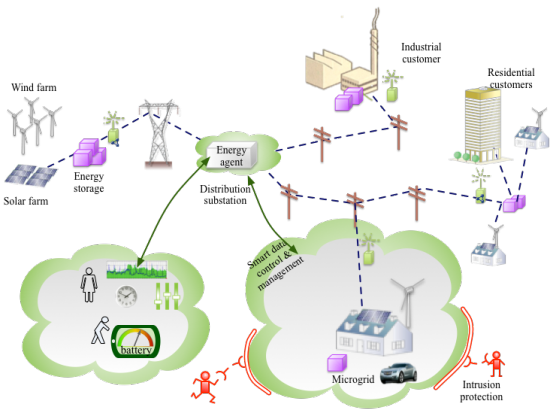
The part will further address potential security threats, here given for the future smart grid
When the future Smart Grid consists of Prosumers (Consumers, who might also be Producers) with different energy sources, the grid will become more unstable.
1.1
Machine-readable Descriptions
- Establish system description examples of systems,
- Describing Security and Security Functionality in a semantic way
Application-driven security goals
- From industrial examples, establish the functional requirements. Example: switch-off time of power circuits less than 10 ms
- from the functional requirements
- establish
- Establish application-driven security goals as well as the semantics of your system
Perform Multi-Metrics Analysis
- Generate matrices to describe the security impact of components and sub-systems, and perform a multi-metrics analysis to establish the system security
- Analyze application goal versus system security and suggest improvements