Difference between revisions of "TEK5530"
Josef.Noll (Talk | contribs) |
Josef.Noll (Talk | contribs) (→L10-L15) |
||
| (342 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
{{Course | {{Course | ||
|Title=Measurable Security for the Internet of Things | |Title=Measurable Security for the Internet of Things | ||
| − | |Abstract= | + | |Abstract=The course provides a methodology for measurable security, privacy, and dependability of industrial systems. Based on e.g. a smart grid example we will establish and develop the methodology to perform a multi-metrics analysis from components to sub-systems to systems. The course will allow you to compare security-related application goals with the results from the system analysis. |
| − | |News=Lectures on | + | |News=Lectures on Tuesdays 09:15-12:00 starting from . The course is given physical at ITS, meeting room 308 |
| − | |Lecturer=Josef Noll | + | |Lecturer=Josef Noll |
| − | |Organisation= | + | |Organisation=UiO |
| − | |Keywords= | + | |Keywords=Security, Network Security, Sensor Security, Sensor networks, Energy monitoring, Energy, Resillient Energy Networks, |
| − | |Objective= | + | |Objective=After completing the course you will be able to: |
| − | + | * Describe application-driven security and establish challenges of sensor-driven systems | |
| − | + | * Provide industrial examples, e.g. Smart Grid and automatic meter readings | |
| − | + | * Have an overview of security features and continuous compliance in Amazon Web Services (cloud security) | |
| − | + | * Establish application-driven security goals as well as the semantics of your system | |
| − | + | * Generate matrices to describe the security impact of components and sub-systems, and perform a multi-metrics analysis to establish the system security | |
| − | + | * Analyse application goal versus system security and suggest improvements | |
| − | |ResearchArea= | + | |ResearchArea=Security |
|Type of course=Master | |Type of course=Master | ||
|TitleNO=Målbart sikkerhet for tingenes internett | |TitleNO=Målbart sikkerhet for tingenes internett | ||
| − | |NewsDE= | + | |NewsDE=Messbare Sicherheit für das Internet der Dinge |
| − | |NewsES=Clases todos los Viernes 0900-1200h, comenzando el | + | |NewsES=Clases todos los Viernes 0900-1200h, comenzando el 22 de Enero del 2016. El curso se imparte en UNIK (Aula 308b), con comunicación por video al aula Scheme@Ifi.UiO.no (1251) |
}} | }} | ||
| − | + | {{TOCright}} | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | =Info-2024= | |
| − | + | We will start with a 3h lecture on 16Jan2024 0915-1200h in a hybrid form: Gunnar Randers vei 19 (Bus from Ole Johan Dals hus (Ifi) leaves at 08:25, see https://www.mn.uio.no/its/om/finn-fram/busstider.html) and http://zoom.jnoll.net or https://uio.zoom.us/j/2313898139 | |
| − | + | ||
| − | + | ||
| − | + | The first lecture will present some of the security challenges and the topics of the course, being the basis for a discussion on interests in measurable security (e.g. energy systems, home automation, autonomous operations,....) | |
| − | + | ||
| − | + | ||
| − | + | During the first lecture we'll also discuss during the first day the set-up of the course. | |
| − | = | + | |
| − | + | == Timeline v24 == | |
| − | * | + | Zoom: http://zoom.jnoll.net or https://uio.zoom.us/j/2313898139 |
| − | * | + | |
| − | * | + | Contact and info |
| − | * | + | * http://Canvas.uio.no or the http://its-wiki.no/wiki/TEK5530 |
| − | * | + | |
| − | * | + | '''Note: Please remind us to take Zoom video recording.''' <br/> |
| − | * | + | <!--- |
| − | * | + | ''Upload: https://kursopplasting.uio.no/?emne=TEK5530&semesterId=24v&terminNr=2''' ---> |
| − | * | + | <!--- Video recording will be available at https://www.uio.no/studier/emner/matnat/its/TEK5530/v23/forelesningsvideoer/ ---> |
| − | + | ||
| − | * | + | == L1-L3 == |
| − | * | + | <!--- {{Large|TEK5530 is performed as project work in spring 2023}} ---> |
| + | * 16Jan L1 Intro, topics, organization (Josef) [[Media:TEK5530-L1_v24.pdf]] | ||
| + | ** Industrial tools for security assessment, see https://expertinsights.com/insights/the-top-10-iot-securitytools/ | ||
| + | * 23Jan L2 Internet of Things [[Media:TEK5530-L2_v24.pdf]] | ||
| + | ** IoT security functionality: https://its-wiki.no/wiki/IoTSec:Smart_Meter_Connectivity | ||
| + | ** Master/PhD AI assessment of Exposure & Impact IoT automation infrastructure (language processing) | ||
| + | |||
| + | * 30Jan L3 Security in the Internet of Things [[Media:TEK5530-L3_v24.pdf]] | ||
| + | ** Paper selection from [[TEK5530/List_of_papers]] | ||
| + | ** Theme: "Measurable Security for the Internet of Things" | ||
| + | ** Discussion on Group Work | ||
| + | ** select a paper and send info on "which paper" to Josef | ||
| + | |||
| + | == L4-L6 == | ||
| + | |||
| + | * 6Feb2024 L4 Security Semantics [[Media:TEK5530-L4-SecuritySemantics_h24.pdf]] | ||
| + | ** group work ideas | ||
| + | |||
| + | * 13Feb2024 L5 Paper presentations, see [[TEK5530/List of papers]] & Intro Multi-Metrics Method [[Media:TEK5530-L6_MultiMetrics_h24.pdf]] | ||
| + | |||
| + | |||
| + | * 20Feb2024 L6 Group work ideas Please prepare the scenario description for your home scenario, with | ||
| + | : a) a description of applications in the home (e.g. web browsing, home control, office applications, communications, ...), and | ||
| + | : b) establish the security and privacy (s,p) requirements for your application | ||
| + | |||
| + | == L7-L9 == | ||
| + | [[File:TEK5530_security_checklist.png|300px|right|thumb|''Security processes and assessment criteria'']] | ||
| + | * 27Feb2024 L7 Paper presentation (remaining papers) and "Walk through" Multi-Metrics, [[Media:TEK5530-L7_WalkThrough_h24.pdf]] & remaining slides [[Media:TEK5530-L6_MultiMetrics_h24.pdf]] | ||
| + | |||
| + | * 5Mar2024 L8 Impact/Exposure Risk Matrix assessment [[Media:TEK5530-L8_Impact-Exposure-Risk_h24update.pdf]] '''updated 19Mar2024''' | ||
| + | :: read more about the security classification model at the PhD of [[Manish_Shrestha]], or register at https://light-sc.tech to gain access | ||
| + | * 12Mar2024 L9 Applicability of Impact/Exposure Risk Matrix and Multi-Metrics [[Media:TEK5530-L9_Applicability_h24.pdf]] | ||
| − | = | + | == L10-L15 == |
| − | * | + | * 19Mar2024 L10 Key exchange and authentication in mobile systems (GSM, UMTS) - [[Media:TEK5530-L10-MobileSecurity_h24.pdf]] |
| − | + | ** [[Media:TEK5530-Gruppearbeid-ideer.pdf]] Ideer om gruppearbeid, fokus på sikkerhetsarkitetur i strømkontrolle hos en kommune | |
| − | * | + | ** relatert til L8 (protection) og L10 slide 34 "assume zero-security infrastructure" |
| − | * | + | |
| − | + | * 26Mar2024 - Påskeferie | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | * 2Apr2024 L11 Zero-trust architecture | |
| − | * | + | |
| + | * 9apr2024 L12 Gruppearbeid - (ingen forelesning) | ||
| − | = | + | * 16apr2024 L13 |
| − | + | ||
| − | + | * 23Apr2024 L14 (conflict for Josef?) | |
| − | | | + | |
| − | + | * 30Apr2024 L15 Presentation of group work | |
| − | | order= | + | |
| − | | | + | * 7May2024 L15 Rehearsel and questions to course |
| − | + | ||
| + | |||
| + | ------ | ||
| + | |||
| + | == Papers & Group work == | ||
| + | * '''[[TEK5530/List of papers|TEK5530 - List of papers]]''', [[Search_for_literature|Guide on how to search for Literature]] | ||
| + | * '''[[TEK5530/Group_work|TEK5530 - Ideas for group work]]''' including own assessment | ||
| + | |||
| + | == Exam 2024 == | ||
| + | '''Exam on Tir 21May2024 will be performed as an oral exam, | ||
| + | Please '''use frameadate https://framadate.org/TEK5530-exam to select your time slot ''' (tbc) | ||
| + | * | ||
| + | |||
| + | As discussed, the exam will consist of 3 parts: | ||
| + | * Part 1: Present your group-work (8 min) - ''assessment of Security Classes for IoT'' or ''Applying Multi-metrics Method'' or ''risk assessment of 5G maritime communications" to be delivered latest by xxx | ||
| + | * Part 2: Questions to group work (7 min) | ||
| + | * Part 3: Random questions from the lectures (10 min). '''[[TEK5530/List_of_Questions]]''' (''you will pick 3-5 questions'') | ||
| + | |||
| + | [[Media:Sensorveiledning_Assessor_Guidance_TEK5530.pdf|Sensorveiledning - Assessor Guidance - TEK5530 (.pdf)]] | ||
| + | |||
| + | =Course info and lectures in previous years = | ||
| + | * [[TEK5530_Lectures_in_earlier_years]] | ||
| + | |||
| + | Course info | ||
| + | * This course is a combined masters and Phd course (UNIK9750), in 2018 all the lectures will be presented by Gyorgy Kalman. | ||
| + | * The course takes place on Thursdays, 0900-1600ish at ITS (UNIK) in Kjeller. This year double lectures will be given, so that we are using the day efficiently, and everybody is requested to take the tour to Kjeller. Video conferencing is available. Double lectures allows us to have the exam early in the semester so that the students can focus on their other duties in the exam period. A recording of all lectures will be provided and in addition personal follow-up is offered for students, who cannot attend some of the lectures. | ||
| + | * We'll have video streaming: mms://lux.unik.no/401 | ||
| + | * Evaluation is based on a presentation of topics and the implementation of your scenario. | ||
| + | |||
| + | |||
| + | * Group work | ||
| + | Please see the description from 2016: '''[[UNIK4750 Group Work|TEK5530 presentation of your Group Work - (suggestions and criteria)]]''' | ||
| + | I recommend you to form 4 (3-5) person groups. I'm open for any suggestion in selecting the IT infrastructure you would like to analyse. There are not that many groups this year, so you are allowed to use longer time for your presentation. | ||
| + | |||
| + | Examples: | ||
| + | * AMS | ||
| + | * Smart home, home automation | ||
| + | * Implications of GDPR on a specific IoT system | ||
| + | * GDPR on medical IoT | ||
| + | * smart car, vehicle-to-vehicle communication, autopilot | ||
| + | * train control from timetables on tablet to predicting power consumption to order power supply for next month | ||
| + | * ship control, from predictive maintenance to offering cloud storage for pictures taken on the cruise | ||
| + | and so on. | ||
| + | A good delivery from 2018: [[Media:good_example_group_work.pdf]] | ||
| + | |||
| + | It should be composed from several "traditional" IT systems interconnected with some communication solution with one end being quite far from the other one. This is to enable you to decompose it to systems of systems relatively easily. Again, no single right answer, I would like to see your way of thinking. | ||
| + | |||
| + | {{TOCright}} | ||
| + | |||
| + | |||
| + | = Introduction into Internet of Things (IoT) = | ||
| + | This first part will provide the introduction into the Internet of Things (''Lecture 1 - 2''), with industrial examples | ||
| + | * Smart Grid and automatic meter system (AMS) | ||
| + | * Smart Homes with sensors | ||
| + | * Autonomous cars | ||
| + | * Cloud technologies | ||
| + | |||
| + | The part will further address potential security threats (''L3''), through the example of the smart grid. The challenges related to attack surface, legal aspects and relation to office IT security will be presented. | ||
| + | |||
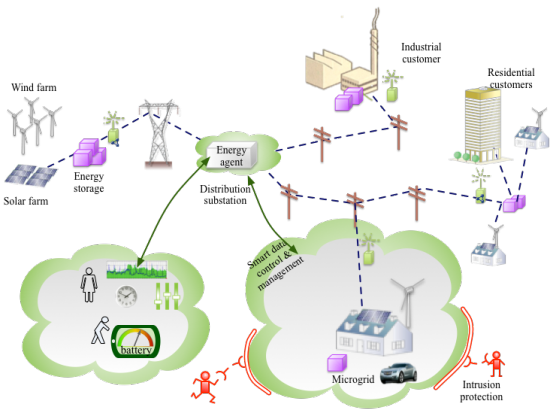
| + | [[File:SmartGrid_future.png|550px]] | ||
| + | |||
| + | The distributed nature of the future (smart) electric grid has its operational, financial, technological and social aspects. In the course we will try to cover all the aspects, with focus on the technological - more precisely: on the communication and security challenges. We expect from the operational viewpont the grid to get more unstable if no compensatory action is done to be the counterweight of renewables and consumers becoming dual role consumer/producers. We will use an example of an automatic meter reading (AMR) and -system (AMS) in ''L4'' to address the security and privacy challenges. | ||
| + | |||
| + | The final part of this first block is addressed through lectures ''L5'' and ''L6'', and will create the mapping from functional requirements towards mapping into technology. Examples of such mapping are the translation of privacy requirements - ''can somebody see from my meter reading if I'm at home'' - towards technology parameters like ''how often are values read and published''. | ||
| + | |||
| + | == Machine-readable Descriptions == | ||
| + | The next block deals with the machine-readable description of security and privacy, security functionality and system of systems through ontologies. | ||
| + | * Establish system description examples of systems, | ||
| + | * Describing Security and Security Functionality in a semantic way | ||
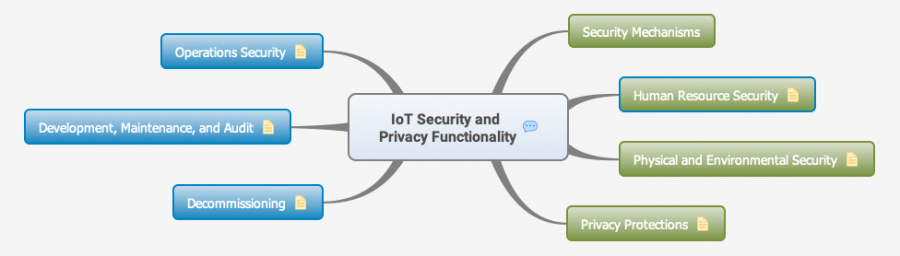
| + | [[File:IoT_Security_and_Privacy_Functionality.png|900px|Security, privacy and dependability functionality (Orig:Owncloud)]]<br/> | ||
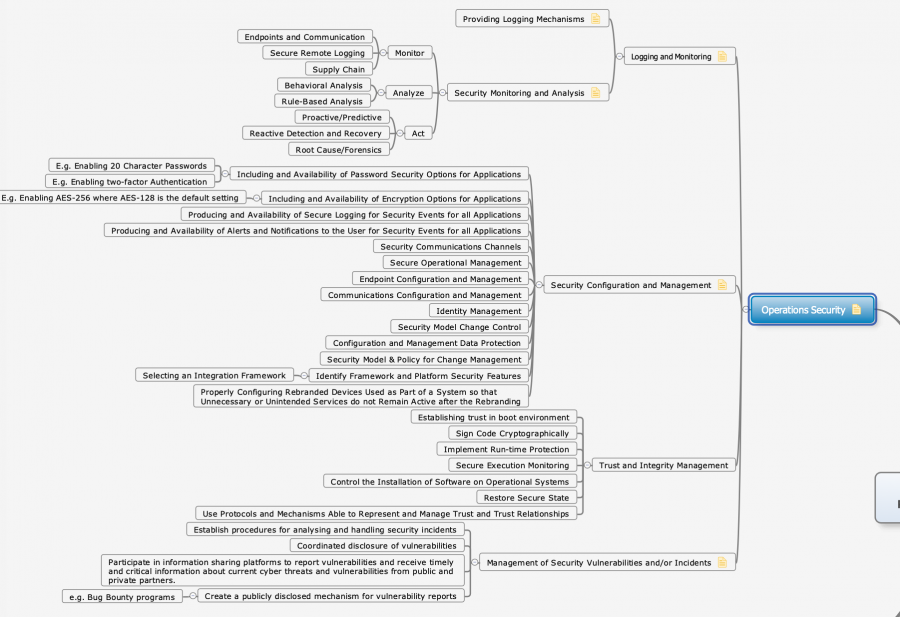
| − | + | [[File:Operations_Security.png|900px]] | |
| − | + | ||
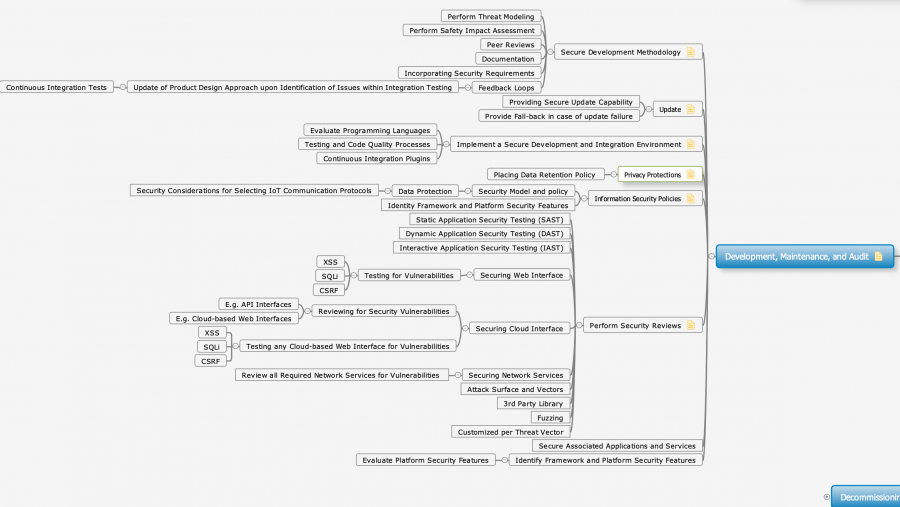
| + | [[File:Dev_Maint_Audit_Security.png|900px]] | ||
| − | + | see all [[IoTSec:Security_and_Privacy_Functionality|SPF.IoTSec.no]] | |
| − | + | ||
| − | + | == Application-driven security goals == | |
| − | + | This block will develop the security goals resulting from applications. | |
| − | = | + | * From industrial examples, establish the functional requirements. Example: switch-off time of power circuits less than 10 ms |
| − | + | * From the functional requirements, select the security and privacy relations | |
| + | * Establish application-driven security goals as well as the semantics of your system | ||
| − | == | + | == Perform Multi-Metrics Analysis == |
| − | + | This last block will analyse industrial examples based on the multi-metrics analysis. | |
| − | * | + | * Generate matrices to describe the security impact of components and sub-systems, and perform a multi-metrics analysis to establish the system security |
| + | * Analyze application goal versus system security and suggest improvements | ||
| − | + | [[Category:TEK5530]] | |
| − | [[Category: | + | |
| − | + | ||
Revision as of 11:03, 19 March 2024
| Wiki for ITS | ||||||
|---|---|---|---|---|---|---|
|
TEK5530 - Measurable Security for the Internet of Things
| TEK5530 | |
|---|---|
| News | Lectures on Tuesdays 09:15-12:00 starting from . The course is given physical at ITS, meeting room 308 |
| Organisation | UiO |
| by | Josef Noll |
| Keywords |
|---|
| Abstract | The course provides a methodology for measurable security, privacy, and dependability of industrial systems. Based on e.g. a smart grid example we will establish and develop the methodology to perform a multi-metrics analysis from components to sub-systems to systems. The course will allow you to compare security-related application goals with the results from the system analysis. |
|---|---|
| Objective (max 350 words) | After completing the course you will be able to:
|
| Keywords | Security, Network Security, Sensor Security, Sensor networks, Energy monitoring, Energy, Resillient Energy Networks |
| Research Area(s) | Security |
| Type of course | Master |
Upload TEK5530.png to see a course picture instead of the banner picture. Edit the page by Special:FormEdit/Course/TEK5530.
To add new lectures, use: Add a lecture
Info-2024
We will start with a 3h lecture on 16Jan2024 0915-1200h in a hybrid form: Gunnar Randers vei 19 (Bus from Ole Johan Dals hus (Ifi) leaves at 08:25, see https://www.mn.uio.no/its/om/finn-fram/busstider.html) and http://zoom.jnoll.net or https://uio.zoom.us/j/2313898139
The first lecture will present some of the security challenges and the topics of the course, being the basis for a discussion on interests in measurable security (e.g. energy systems, home automation, autonomous operations,....)
During the first lecture we'll also discuss during the first day the set-up of the course.
Timeline v24
Zoom: http://zoom.jnoll.net or https://uio.zoom.us/j/2313898139
Contact and info
Note: Please remind us to take Zoom video recording.
L1-L3
- 16Jan L1 Intro, topics, organization (Josef) Media:TEK5530-L1_v24.pdf
- Industrial tools for security assessment, see https://expertinsights.com/insights/the-top-10-iot-securitytools/
- 23Jan L2 Internet of Things Media:TEK5530-L2_v24.pdf
- IoT security functionality: https://its-wiki.no/wiki/IoTSec:Smart_Meter_Connectivity
- Master/PhD AI assessment of Exposure & Impact IoT automation infrastructure (language processing)
- 30Jan L3 Security in the Internet of Things Media:TEK5530-L3_v24.pdf
- Paper selection from TEK5530/List_of_papers
- Theme: "Measurable Security for the Internet of Things"
- Discussion on Group Work
- select a paper and send info on "which paper" to Josef
L4-L6
- 6Feb2024 L4 Security Semantics Media:TEK5530-L4-SecuritySemantics_h24.pdf
- group work ideas
- 13Feb2024 L5 Paper presentations, see TEK5530/List of papers & Intro Multi-Metrics Method Media:TEK5530-L6_MultiMetrics_h24.pdf
- 20Feb2024 L6 Group work ideas Please prepare the scenario description for your home scenario, with
- a) a description of applications in the home (e.g. web browsing, home control, office applications, communications, ...), and
- b) establish the security and privacy (s,p) requirements for your application
L7-L9
- 27Feb2024 L7 Paper presentation (remaining papers) and "Walk through" Multi-Metrics, Media:TEK5530-L7_WalkThrough_h24.pdf & remaining slides Media:TEK5530-L6_MultiMetrics_h24.pdf
- 5Mar2024 L8 Impact/Exposure Risk Matrix assessment Media:TEK5530-L8_Impact-Exposure-Risk_h24update.pdf updated 19Mar2024
- read more about the security classification model at the PhD of Manish_Shrestha, or register at https://light-sc.tech to gain access
- 12Mar2024 L9 Applicability of Impact/Exposure Risk Matrix and Multi-Metrics Media:TEK5530-L9_Applicability_h24.pdf
L10-L15
- 19Mar2024 L10 Key exchange and authentication in mobile systems (GSM, UMTS) - Media:TEK5530-L10-MobileSecurity_h24.pdf
- Media:TEK5530-Gruppearbeid-ideer.pdf Ideer om gruppearbeid, fokus på sikkerhetsarkitetur i strømkontrolle hos en kommune
- relatert til L8 (protection) og L10 slide 34 "assume zero-security infrastructure"
- 26Mar2024 - Påskeferie
- 2Apr2024 L11 Zero-trust architecture
- 9apr2024 L12 Gruppearbeid - (ingen forelesning)
- 16apr2024 L13
- 23Apr2024 L14 (conflict for Josef?)
- 30Apr2024 L15 Presentation of group work
- 7May2024 L15 Rehearsel and questions to course
Papers & Group work
- TEK5530 - List of papers, Guide on how to search for Literature
- TEK5530 - Ideas for group work including own assessment
Exam 2024
Exam on Tir 21May2024 will be performed as an oral exam, Please use frameadate https://framadate.org/TEK5530-exam to select your time slot (tbc)
As discussed, the exam will consist of 3 parts:
- Part 1: Present your group-work (8 min) - assessment of Security Classes for IoT or Applying Multi-metrics Method or risk assessment of 5G maritime communications" to be delivered latest by xxx
- Part 2: Questions to group work (7 min)
- Part 3: Random questions from the lectures (10 min). TEK5530/List_of_Questions (you will pick 3-5 questions)
Sensorveiledning - Assessor Guidance - TEK5530 (.pdf)
Course info and lectures in previous years
Course info
- This course is a combined masters and Phd course (UNIK9750), in 2018 all the lectures will be presented by Gyorgy Kalman.
- The course takes place on Thursdays, 0900-1600ish at ITS (UNIK) in Kjeller. This year double lectures will be given, so that we are using the day efficiently, and everybody is requested to take the tour to Kjeller. Video conferencing is available. Double lectures allows us to have the exam early in the semester so that the students can focus on their other duties in the exam period. A recording of all lectures will be provided and in addition personal follow-up is offered for students, who cannot attend some of the lectures.
- We'll have video streaming: mms://lux.unik.no/401
- Evaluation is based on a presentation of topics and the implementation of your scenario.
- Group work
Please see the description from 2016: TEK5530 presentation of your Group Work - (suggestions and criteria) I recommend you to form 4 (3-5) person groups. I'm open for any suggestion in selecting the IT infrastructure you would like to analyse. There are not that many groups this year, so you are allowed to use longer time for your presentation.
Examples:
- AMS
- Smart home, home automation
- Implications of GDPR on a specific IoT system
- GDPR on medical IoT
- smart car, vehicle-to-vehicle communication, autopilot
- train control from timetables on tablet to predicting power consumption to order power supply for next month
- ship control, from predictive maintenance to offering cloud storage for pictures taken on the cruise
and so on. A good delivery from 2018: Media:good_example_group_work.pdf
It should be composed from several "traditional" IT systems interconnected with some communication solution with one end being quite far from the other one. This is to enable you to decompose it to systems of systems relatively easily. Again, no single right answer, I would like to see your way of thinking.
Introduction into Internet of Things (IoT)
This first part will provide the introduction into the Internet of Things (Lecture 1 - 2), with industrial examples
- Smart Grid and automatic meter system (AMS)
- Smart Homes with sensors
- Autonomous cars
- Cloud technologies
The part will further address potential security threats (L3), through the example of the smart grid. The challenges related to attack surface, legal aspects and relation to office IT security will be presented.
The distributed nature of the future (smart) electric grid has its operational, financial, technological and social aspects. In the course we will try to cover all the aspects, with focus on the technological - more precisely: on the communication and security challenges. We expect from the operational viewpont the grid to get more unstable if no compensatory action is done to be the counterweight of renewables and consumers becoming dual role consumer/producers. We will use an example of an automatic meter reading (AMR) and -system (AMS) in L4 to address the security and privacy challenges.
The final part of this first block is addressed through lectures L5 and L6, and will create the mapping from functional requirements towards mapping into technology. Examples of such mapping are the translation of privacy requirements - can somebody see from my meter reading if I'm at home - towards technology parameters like how often are values read and published.
Machine-readable Descriptions
The next block deals with the machine-readable description of security and privacy, security functionality and system of systems through ontologies.
- Establish system description examples of systems,
- Describing Security and Security Functionality in a semantic way
see all SPF.IoTSec.no
Application-driven security goals
This block will develop the security goals resulting from applications.
- From industrial examples, establish the functional requirements. Example: switch-off time of power circuits less than 10 ms
- From the functional requirements, select the security and privacy relations
- Establish application-driven security goals as well as the semantics of your system
Perform Multi-Metrics Analysis
This last block will analyse industrial examples based on the multi-metrics analysis.
- Generate matrices to describe the security impact of components and sub-systems, and perform a multi-metrics analysis to establish the system security
- Analyze application goal versus system security and suggest improvements