TEK5530 Lectures in earlier years
| Wiki for ITS | ||||||
|---|---|---|---|---|---|---|
|
Lectures in TEK5530 in earlier years
Timeline v22
- 20Jan L1 Intro, topics, organization (Josef) Media:TEK5530-L1_v22.pdf
- 27Jan L2 Internet of Things
- 03Feb L3 Security of IoT + Paper list
- 10Feb L4 Smart Grid, Automatic Meter Readings
- 17Feb L5 Practical implementation of ontologies
- 24Feb L6 Multi-Metrics Method for measurable Security
- 03Mar L7 Communication in Smart Grid, Smart home and IoT
- 10Mar L8 Intrusion detection
- 17Mar L9 Paper analysis with 25 min presentation
- 24Mar L10 Paper analysis with 25 min presentation/Risk analysis tool
- 31Mar L11 Cloud Basics
- 07Apr L12 Cloud security and IoT
- 21Apr L13 TBD
- 28Apr L14 TBD
- 05May L15 Selected recent topics from IoT security
- 12May L16 Wrap-up of the course
- EXAM: TBD
Lectures in TEK5530 - 2021
21Jan L1 & L2 (Josef Noll) 09:15-16:00h
- L1: Introduction (Josef Noll) Media:TEK5530-L1_v21.pdf
- L2: Internet of Things (Josef Noll) Media:TEK5530-L2_v21.pdf
- Paper used for the group work on the lecture: Atzori et al. Survey Internet of Things
- Video introduction: IBM introduction to IoT, TED talk of John Barrett Introduction to Amazon AWS IoT
28.01 L3 & L4 György Kálmán
- L3: Security of the Internet of Things Media:TEK5530-L3_v21.pdf
- L4: Smart Grid and AMS Media:TEK5530-L4_v21.pdf
04.02 L5 Semantic Technologies & L6 Multi-Metrics Method
- L5: Semantic Technologies - Ontologies Media:TEK5530-L5.pdf
- see: intro to semantics https://www.youtube.com/watch?v=4x_xzT5eF5Q
- enjoy: ordering a piza https://www.youtube.com/watch?v=RNJl9EEcsoE
- details on Ontologies: https://www.slideshare.net/marinasantini1/09-semantic-webontologies?qid=8b178746-ea3c-48db-b4f6-6bc9b0923d9b
- IoT Life-Cycle Security, see: IoTSec:Security_and_Privacy_Functionality with document IoT Security and Privacy Functionality Life Map (.pdf)
- L6: Multi-Metrics Method for measurable Security Media:TEK5530-L6_Multi-Metrics.pdf
- Security threats/attacks on IoT by Tom Gaffney, F-Secure https://eyenetworks.no/wp-content/uploads/2019-shared-insights-tom-gaffney-f-secure-1.pdf
- Mirai attack capabilities IoTSec:The_Denial_of_Service_Attack_from_IoT_devices
- Privacy label, see Privacy_Label
11.02 L7 Multi-Metrics on an AMR sub-system & L8 System Security and Privacy analysis
- Multi-Metrics Analyis, link to owncloud folder: https://owncloud.basicinternet.org/index.php/s/8vgAusswDepivTn
- containing three files: MultiMetrics_CarPrivacy.xlsx & SPD_SmartGrid_Multi-Metrics.xlsx & combined SPD_Multi-Metrics.numbers (apple numbers with combined analysis)
- L7: Multi-Metrics Weighting of an AMR sub-system Media:TEK5530-L7.pdf
- AMS topology: Media:AMI_topology.pdf
- L8: System Security and Privacy analysis Media:TEK5530-L8.pdf
18.02
- L9 Paper presentations
- L10: Security Controls Media:TEK5530-L10.pdf
- 25.02
- L11 Communication in Smart Grid and MS Threat Management tool Media:TEK5530-L11_comm.pdf
- L12 Intrusion Detection Media:TEK5530-L12_IDS.pdf
- 04.03
- L13 & L14 Cloud basics, security and IoT Media:TEK5530-L13-14_cloud.pdf
- 11.03 L15 & Rehearsal Media:TEK5530-L15_RecentTopics_Rehearsel.pdf, see also Questions for the exam
- EXAM: 25Mar2021
Lectures in TEK5530 - 2020
- 16Jan (Gyorgy Kalman & Josef Noll) 09:15-16:00h
- L1: Introduction (Josef Noll) Media:TEK5530-L1.pdf
- L2: Internet of Things (Gyorgy Kalman) Media:TEK5530-L2.pdf Media:TEK5530-L2-notes.pdf
- Paper used for the group work on the lecture: Atzori et al. Survey Internet of Things
- Video introduction: IBM introduction to IoT, TED talk of John Barrett Introduction to Amazon AWS IoT
- 23.01 (Gyorgy Kalman)
- L3: Security of IoT + Paper list Media:TEK5530-L3.pdf
- L4: Smart Grid, Automatic Meter Readings Media:TEK5530-L4.pdf
- 06.02 (Josef Noll)
- L5: Semantic Technologies - Ontologies Media:TEK5530-L5.pdf - Whiteboard Notes: Media:TEK5530-L5-L6-Notes.pdf
- see: intro to semantics https://www.youtube.com/watch?v=4x_xzT5eF5Q
- enjoy: ordering a piza https://www.youtube.com/watch?v=RNJl9EEcsoE
- details on Ontologies: https://www.slideshare.net/marinasantini1/09-semantic-webontologies?qid=8b178746-ea3c-48db-b4f6-6bc9b0923d9b
- IoT Life-Cycle Security, see: IoTSec:Security_and_Privacy_Functionality with document IoT Security and Privacy Functionality Life Map (.pdf)
- L6: Multi-Metrics Method for measurable Security Media:TEK5530-L6_Multi-Metrics.pdf
- Security threats/attacks on IoT by Tom Gaffney, F-Secure https://eyenetworks.no/wp-content/uploads/2019-shared-insights-tom-gaffney-f-secure-1.pdf
- Mirai attack capabilities IoTSec:The_Denial_of_Service_Attack_from_IoT_devices
- Privacy label, see Privacy_Label
- 13.02 (Josef Noll)
- L7: Multi-Metrics Weighting of an AMR sub-system Media:TEK5530-L7.pdf - Handouts L7 & L8 Media:TEK5530-L7-L8.pdf
- AMS topology: Media:AMI_topology.pdf
- L8: System Security and Privacy analysis Media:TEK5530-L8.pdf
- 20.02 (Josef Noll) 10:00h L9-10: Paper analysis with 25 min presentation - Media:TEK5530_Security_Handouts.pdf
- Security Classification for Smart Grid: Media:Security_Classification_for_Smart_Grid.pdf
- Paper by Manish Shrestha on Security Classification for Home Automation
- Enhanced security classification methodology (Maunya)
- Tool for Security Class evaluationfor SCOTT WP21
- 27.02 no lecture
- 05.03 (Gyorgy Kalman)
- L11: Service implications on functional requirements Media:TEK5530-L11.pdf
- L12: Intrusion Detection Media:TEK5530-L12.pdf
- 12.03.2020 no lecture due to Corona regulations
- 19.03 (Gyorgy Kalman)
- L15: Cloud basics and cloud architecture
- L16: Cloud security, IoT and service examples from AWS Media:TEK5530-L15-L16.pdf
- 26.03 (Gyorgy Kalman)
gotomeeting, ID 725-796-213
- L13: Technology mapping Media:TEK5530-L13.pdf
- L14: Communication and security in current industrial automation Media:TEK5530-L14.pdf
- Exam on 22Apr2020 starting from 09:30h
Lectures in 2019
Contents
- 1 Lectures in TEK5530 in earlier years
- 2 Lectures in TEK5530 - 2021
- 3 Lectures in TEK5530 - 2020
- 4 Lectures in 2019
- 5 Info - 2018
- 6 Lectures in UNIK4750 - 2018
- 7 Info - 2017
- 8 Introduction into Internet of Things (IoT)
- 9 Lecture overview with keywords
- 10 Lectures in UNIK4750 - 2017
- 11 Info - 2016
- 12 Lectures in UNIK4750 - 2016
17Jan - L1: Introduction - Handouts Media:TEK5530 - L1 Introduction.pdf
- Tesla battery with high earnings when balancing the Australian grid
- Tesla battery paid back third of investment in a year
- eHealth predictions for 2019
24Jan - L2: Internet of Things - Handouts Media:TEK5530 - L2 IoT.pdf
- Paper used for the group work on the lecture: [1]
- Video introduction: IBM introduction to IoT, TED talk of John Barrett Introduction to Amazon AWS IoT
31Jan - L3: Security in the Internet of Things Media:TEK5530 - L3 IoTsec.pdf
- Advantech Internet Gateway Vulnerability
- ICS-CERT alerts
- OWASP IoT Project
- Data leakage from fitness tracker app reveals base locations
07Feb- L4: Smart Grid and AMS Media:TEK5530 - L4 smart_grid_ams.pdf and L5: Service Implications on Functional Requirements Media:TEK5530 - L5 service_implications.pdf
14Feb- L6: Technology mapping Media:TEK5530 - L6_tech_mapping.pdf and L9: Top 20 critical security controls Media:TEK5530 - L9_top_critical_controls.pdf
14Feb- L6: Technology mapping Media:TEK5530 - L6_tech_mapping.pdf and L9: Top 20 critical security controls Media:TEK5530 - L9_top_critical_controls.pdf
21Feb - Winter holiday, no lecture
28Feb - L10: Intrusion detection Media:TEK5530 - L10_intrusion_detection.pdf
07March - L13: Communication and security in current industrial automation Media:TEK5530 - L13-hardening_automation.pdf and L14: Cloud basics and cloud architecture Media:TEK5530 - L14_cloud_basics.pdf
14Mar - L11 & L12
- L11: Multi-Metrics method for measurable security and privacy- Handouts Media:TEK5530-L11_Multi-Metrics.pdf, including discussion of privacy scenarios
- for analysis, see: # I. Garitano, S. Fayyad, J. Noll, «Multi-Metrics Approach for Security, Privacy and Dependability in Embedded Systems», Wireless Pers. Commun. 81, pp1359-1376 (2015)
- L12: System Security and Privacy analysis, weighting of components and sub-systems - Handouts Media:TEK5530-L12_System_Security_Privacy.pdf
- Paper describing the smart grid security and privacy analysis is available from Multi-Metrics_approach, or directly as: J. Noll, I. Garitano, S. Fayyad, E. Åsberg, H. Abie, «Measurable Security, Privacy and Dependability in Smart Grids», Journal of Cyber Security, 3_4, (2015) -> http://riverpublishers.com/journal/journal_articles/RP_Journal_2245-1439_342.pdf
- Notes from Whiteboard: Media:201903_TEK5530_L11-L12.pdf, Video recording, only WhiteBoard
21Mar - L15-16: Cloud architecture, security and IoT Media:TEK5530 - L15-16-architecture_security_iot.pdf
28Mar - L17 Wrap-Up Media:TEK5530 - L17-wrap_up.pdf Questions for the exam: Media:TEK5530 - exam_questions.pdf
Video recordings (2018, valid for 2019):
L1: Introduction
- Video: [2]
L2: Internet of Things
- Video : [3]
L3: Security of the Internet of Things
- Video: [4]
L4: Smart grid and Automatic Meter Readings
- Video : [5]
L5: Service Implications on Functional Requirements
- Video: [6]
L6: Technology Mapping
- Video : [7]
Info - 2018
Lectures in UNIK4750 - 2018
18Jan - L1: Introduction - Handouts Media:UNIK4750-L1_Introduction 2018-01-18.pdf
25Jan - L2: Internet of Things - Handouts Media:UNIK4750-L2-Internet_of_Things-2018.pdf
- Paper used for the group work on the lecture: [9]
- Video introduction: IBM introduction to IoT, TED talk of John Barrett Introduction to Amazon AWS IoT
- Video : [10]
25Jan - L3: Security of the Internet of Things - Handouts Media:UNIK4750-L3_Security in the Internet of Things - 2018.pdf
- Video: [11]
- UNIK4750/List of papers - 2018, Guide on how to search for Literature
- Advantech Internet Gateway Vulnerability
- ICS-CERT alerts
- OWASP IoT Project
- Data leakage from fitness tracker app reveals base locations
01Feb - No lecture because of sickness
08Feb - L4: Smart grid and Automatic Meter Readings - Handouts Media:UNIK4750-L4_Smart Grid and AMS - 2018.pdf
- Video : [12]
08Feb - L5: Service Implications on Functional Requirements - Handouts Media:UNIK4750-L5_Service implications on functional requirements - 2018.pdf
- Video: [13]
15Feb - L6: Technology Mapping - Handouts Media:UNIK4750-L6_Technology_mapping_2018.pdf
- Video : [14]
15Feb - L7: Security semantics - Handouts Media:UNIK4750-L7_security_semantics_2018.pdf
- Video (2017): [15]
- Video (full semantics coverage, 2016 by Josef Noll): [16]
- Bonus short lecture: Media:Communication_and_security_in_automation-2018.pdf
8Mar - L10: Multi-Metrics method for measurable security and privacy- Handouts Media:UNIK4750-L10_Multi-Metrics.pdf, including discussion of privacy scenarios
- for analysis, see: # I. Garitano, S. Fayyad, J. Noll, «Multi-Metrics Approach for Security, Privacy and Dependability in Embedded Systems», Wireless Pers. Commun. 81, pp1359-1376 (2015)
- L11: System Security and Privacy analysis, weighting of components and sub-systems - Handouts Media:UNIK4750-L11_System_Security_Privacy.pdf
- Paper describing the smart grid security and privacy analysis is available from Multi-Metrics_analysis, or directly as: J. Noll, I. Garitano, S. Fayyad, E. Åsberg, H. Abie, «Measurable Security, Privacy and Dependability in Smart Grids», Journal of Cyber Security, 3_4, (2015) -> http://riverpublishers.com/journal/journal_articles/RP_Journal_2245-1439_342.pdf
- Notes from Whiteboard: Media:201803_UNIK4750_L10-L11.pdf
- Video: [17]
15Mar - L13 Guest lecture by Mohammad Chowdhury from ABB, Media:Securing_Industrial_Automation_and_Control_Systems.pdf
- Video: [18]
L14 - System Security and Privacy Media:L14_System_security_privacy.pdf
- Video: [19]
22Mar - L17 Intrusion Detection Systems and Cloud Security Media:L17_IDS_and_Cloud.pdf
- Video: [20]
L18 - Wrap-up Media:L18_Wrap_up.pdf
- Video: [21]
Exam questions (minor update from 2017): Media:Questions_UNIK4750_2018_students.pdf
Info - 2017
- This course is a combined masters and Phd course (UNIK9750), in 2017 all the lectures will be presented by Gyorgy Kalman.
- The course takes place on Thursdays, 0900-1600ish at ITS (UNIK) in Kjeller. This year double lectures will be given, so that we are using the day efficiently, and everybody is requested to take the tour to Kjeller. Video conferencing is still available.
- We'll have video streaming: mms://lux.unik.no/401
- Evaluation is based on a presentation of topics and the implementation of your scenario.
Introduction into Internet of Things (IoT)
This first part will provide the introduction into the Internet of Things (Lecture 1 - L2), with industrial examples
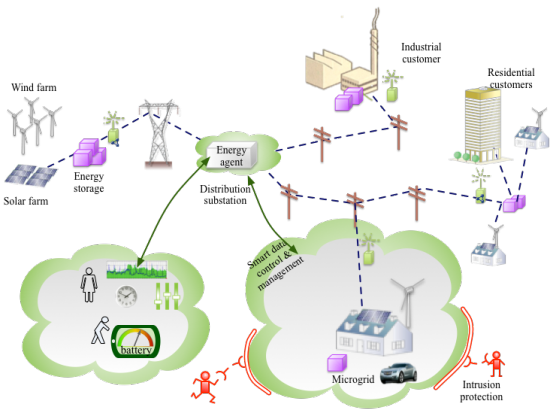
- Smart Grid and automatic meter system (AMS)
- Smart Homes with sensors
- Wireless System upgrade of cars
The part will further address potential security threats (L3), here given for the future smart grid.
When the future Smart Grid consists of Prosumers (Consumers, who might also be Producers) with different energy sources, the grid will become more unstable. We will use an example of an automatic meter reading (AMR) and -system (AMS) in L4 to address the security and privacy challenges.
The final part of this first block is addressed through lectures L5 and L6, and will create the mapping from functional requirements towards mapping into technology. Examples of such mapping are the translation of privacy requirements - can somebody see from my meter reading if I'm at home - towards technology parameters like how often are values read and published.
Machine-readable Descriptions
The next block deals with the machine-readable description of security and privacy, security functionality and system of systems through ontologies.
- Establish system description examples of systems,
- Describing Security and Security Functionality in a semantic way
Application-driven security goals
This block will develop the security goals resulting from applications.
- From industrial examples, establish the functional requirements. Example: switch-off time of power circuits less than 10 ms
- From the functional requirements, select the security and privacy relations
- Establish application-driven security goals as well as the semantics of your system
Perform Multi-Metrics Analysis
This last block will analyse industrial examples based on the multi-metrics analysis.
- Generate matrices to describe the security impact of components and sub-systems, and perform a multi-metrics analysis to establish the system security
- Analyze application goal versus system security and suggest improvements
Lecture overview with keywords
this section is automatically filled in based on the information on this MediaWiki
Lectures in UNIK4750 - 2017
19Jan - L1: Introduction - Handouts Media:UNIK4750-L1-Introduction-2017.pdf
- Video: [22]
26Jan - L2: Internet of Things - Handouts Media:UNIK4750-L2-Internet_of_Things-2017.pdf
- Video introduction: IBM introduction to IoT, TED talk of John Barrett
- Link to IoT paper referenced on the lecture slide: L. Atzori et al., The Internet of Things: A survey
- Video : [23]
02Feb - L3: Security of the Internet of Things - Handouts Media:UNIK4750-L3_Security in the Internet of Things - 2017.pdf
- Video: [24]
- UNIK4750/List of papers - 2017, Guide on how to search for Literature
- Advantech Internet Gateway Vulnerability
- ICS-CERT alerts
- OWASP IoT Project
09Feb - L4: Smart Grid, Automatic Meter Readings (AMR) - Handouts Media:UNIK4750-L4-Automatic_Meter_Readings-2017_examples.pdf
- Relevant presentation: On Smart Cities, Smart Energy, And Dumb Security
- Presentation about StatNett Media:Program FoU konferansen 2015.pdf
09Feb - L5: Service implications on functional requirements - Handouts Media:UNIK4750-L5-Service_Implications-2017.pdf
- Video: [25]
- One of my previous lectures on realtionship between security and safety: Media:Security_and_safety.pdf
- The Rocky Relationship Between Safety and Security by ABB
16Feb - L6: Technology Mapping - Handouts Media:UNIK4750-L6-Technology_mapping-2017.pdf
- Video: [26]
16Feb - L7: Security Semantics - Handouts Media:UNIK4750-L7-Security_semantics-2017.pdf
- Video: [27]
- For full semantics coverage please see Josef's lecture from 17th March 2016
- Bonus short lecture: Media:Communication_and_security_in_automation.pdf
23Feb - Vinterferie
02March - L8-9 Paper presentations 1
- Video: [28]
09March - L10-11 Paper presentations 2
- Video: [29]
16March - L12: Multi-Metrics method for measurable security - Handouts Media:UNIK4750-L12_Multi-Metrics.pdf
16March - L13: System Security and Privacy analysis - Handouts Media:UNIK4750-L13_System_Security_Privacy.pdf
- Video: [30]
23March - L14: Weighting in Multi-Metrics Method Media:UNIK4750-L11_Weighting_AMR.pdf - Lecture Notes L11
23March - L15: Real-world examples (Guest lecture by Mohammad Chowdhury) - Media:UNIK4750-Guest-Lecture_ABB_Chowdhury.pdf
- Video: [31]
30March - no lecture
06April - L16: Group work presentation
06April - L17: wrap-up, Media:UNIK4750-L17 Wrap Up.pdf Media:Questions_UNIK4750_2017_students.pdf
- Video: [32]
13April - Easter holiday
20April - Exam
Info - 2016
- This course is a Master course. Please visit UNIK9750 for the PhD version of the course.
- The course takes place on Thursdays, 0900-1200h at UNIK. A video communication is available to Ifi, Room Scheme@Ifi.UiO.no (room 1251), see check: Video_conference
- We'll have video streaming: mms://lux.unik.no/401
- Evaluation is based on a presentation of topics and the implementation of your scenario.
Lectures in UNIK4750 - 2016
21Jan - L1: Introduction G,J - Handouts Media:UNIK4750-L1-Introduction.pdf
- Lecture Notes Media:UNIK4750-L1-LectureNotes.pdf
- Podcast (Audio): Download lecture 1
- Video Podcast: Lecture 1 NB! If you are using Mac and have problem playing the video please first disable your firewall!
28Jan - L2: Internet of Things J - Handouts Media:UNIK4750-L2-Internet_of_Things.pdf
- Video introduction: IBM introduction to IoT, TED talk of John Barrett
- Internet of Things Paper (.pdf)
- Lecture Notes Media:UNIK4750-L2-LectureNotes.pdf
- Podcast (Audio - first 30 minutes): Download lecture 2
- Video Podcast: Lecture 2
4Feb - L3: Security in IoT G - Paper selection - Handouts Media:UNIK4750-L3-Security_IoT.pdf
- UNIK4750/List of papers, Guide on how to search for Literature
- Devon conference paper (.pdf)
- no lecture notes
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160204.wmv
11Feb - L4: Smart Grid, Automatic Meter Readings (AMR) G - Handouts Media:UNIK4750-L4-Automatic_Meter_Readings.pdf
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160211.wmv
18Feb - L5: Service implications on functional requirements G,(J) - Handouts Media:UNIK4750-L5-Service_Implications.pdf
- Podcast (Audio): Download lecture 5
- Video Podcast: mms://lux.unik.no/2016/UNIK4750-GK/UNIK-20160218.wmv Unfortunately due to technical problems the first half of the lecture is not recorded but you can use this link to download an audio file which covers the whole lecture.
3Mar - L6: Technology mapping G,(J) - Handouts Media:UNIK4750-L6-Technology_mapping.pdf,
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160303.wmv
- Paper: 10 differences between ICS and IT systems
- Paper: Practical applications of Lightweight Block Ciphers to Secure EtherNet/IP Networks
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160303.wmv
10Mar - L7: UNIK4750 Paper analysis with 15-20 min presentation, evaluation criteria
17Mar - L8: Security Semantics J - Handouts Media:UNIK4750-L8-Security_Semantics.pdf
- Lecture Notes Media:UNIK4750-L8-LectureNotes.pdf
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160317.wmv
31Mar - L9: Logical binding - industrial example J, Guest lecturer: Mushfiq Chowdhury - Handouts: Media:UNIK4750-L9-handouts.pdf
- Media:20160331-L9-Lecture_notes.pdf Lecture notes
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160331.wmv
- Media:2016031-Project-Ideas.pdf - Information on your Project
7Apr - L10: Multi-Metrics Method for measurable Security J - Handouts Media:UNIK4750-L10-Multi-Metrics.pdf,
- last slides from Security Semantics: Media:UNIK4750-L8-Security_Semantics.pdf
- Paper describing the approach: Multi Metrics Approach for Embedded Systems (.pdf on Research Gate)
- Media:20160407-L10-Lecture_notes.pdf Lecture notes
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160407.wmv
14Apr - L11: Multi-Metrics Weighting of an AMR sub-system J - Handouts L11 Media:UNIK4750-L11-AMR-weight.pdf
- Paper describing the approach: Multi Metrics Approach for Smart Grids
- Media:20160414-L11-Lecture_notes.pdf Lecture notes
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160414.wmv
21Apr - L12: System Security and Privacy analysis J - Handouts L12 Media:UNIK4750-L12-Security-Privacy_classes.pdf
- Media:20160421-L12-Lecture_notes.pdf Lecture notes
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160421.wmv
28Apr - L13: Intrusion-detection in industrial environments - G - Handouts L13 Media:UNIK4750-L13-Intrusion_detection.pdf
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160428.wmv
12May - L14: Real world examples - IoTSec infrastructure J - - Handouts L14 Media:UNIK4750-L14-IoTSec_infrastructure.pdf
- Media:20160421-L14-IoTSec_infrastructure.pdf Lecture notes
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160512.wmv
19May - L15: Real world IoT service evaluation; UNIK4750 presentation of your Group Work - (suggestions and criteria)
- Video Podcast: mms://lux.unik.no/UNIK4750-GK/2016/UNIK-20160519.wmv
26May - time for exam preparation (no lecture)
Thursday 2Jun or Wednesday 8Jun - Exam G,J