Difference between revisions of "IoTSec:Security and Privacy Functionality"
From its-wiki.no
Josef.Noll (Talk | contribs) (→Security, Privacy and Dependability Functionality) |
Josef.Noll (Talk | contribs) m (→Security, Privacy and Dependability Functionality) |
||
| Line 2: | Line 2: | ||
{{hasKeywords | {{hasKeywords | ||
|Keywords=Security, Privacy, Dependability, Security Functionality}} | |Keywords=Security, Privacy, Dependability, Security Functionality}} | ||
| + | The starting point for the security listing is the representation of [[System of Systems]] through the [[Multi-Metrics analysis]]. Applications running on the systems typically have functional and non-functional requirements, which also addresses security and privacy requirements. | ||
The page is exported from see [[File:SPD_Functionality.doc]] | The page is exported from see [[File:SPD_Functionality.doc]] | ||
Revision as of 09:16, 29 March 2017
| Security in IoT for Smart Grids | |||||||
|---|---|---|---|---|---|---|---|
|
Security, Privacy and Dependability Functionality
Keywords: Security, Privacy, Dependability, Security Functionality
The starting point for the security listing is the representation of System of Systems through the Multi-Metrics analysis. Applications running on the systems typically have functional and non-functional requirements, which also addresses security and privacy requirements.
The page is exported from see File:SPD Functionality.doc
Link: https://owncloud.unik.no/index.php/apps/files/ajax/download.php?dir=%2F1-Projects%2FIoTSec-IKTPluss&files=SPD-Functionality.xmind
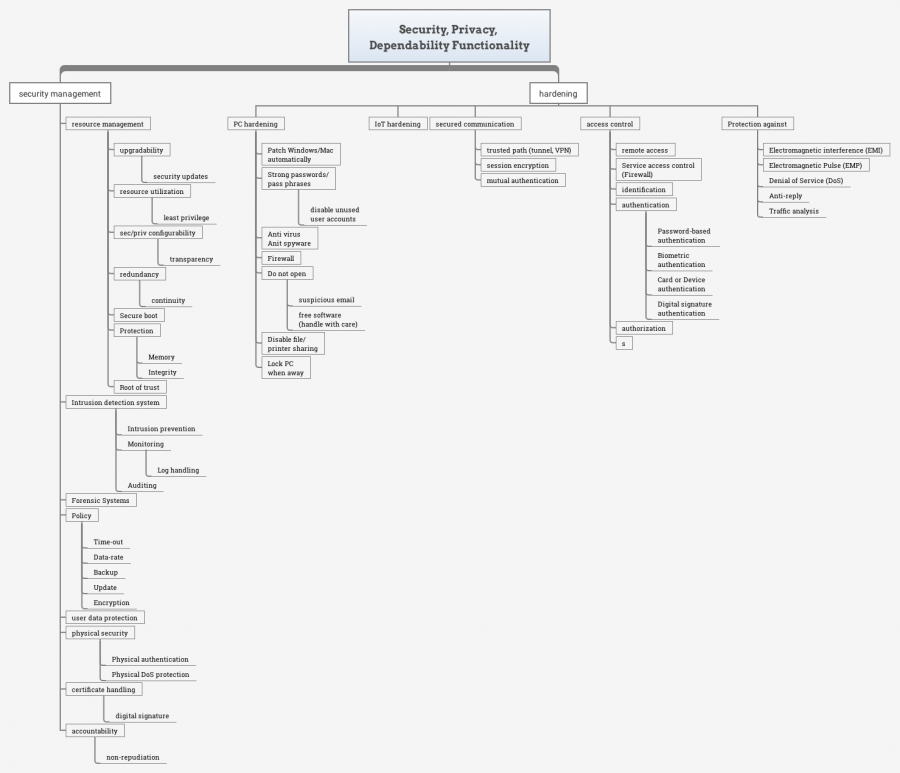
Security and Privacy Functionality paragraphs
1. security management
- 1.1. Intrusion detection system
- 1.1.1. Intrusion prevention
- 1.1.2. Monitoring, Log handling
- 1.1.3. Auditing
- 1.2. Policy
- 1.2.1. Time-out
- 1.2.2. Data-rate
- 1.2.3. Backup
- 1.2.4. Update
- 1.2.5. Encryption
- 1.3. user data protection
- 1.4. physical security
- 1.4.1. Physical authentication
- 1.4.2. Physical DoS protection
- 1.5. certificate handling
- 1.5.1. digital signature
- 1.6. accountability
- 1.6.1. non-repudiation
2. hardening
- 2.1. PC hardening
- 2.1.1. Patch Windows/Mac automatically
- 2.1.2. Strong passwords/ pass phrases
- disable unused
- user accounts
- 2.1.3. Anti virus/Anit spyware
- 2.1.4. Firewall
- 2.1.5. Do not open
- suspicious email
- free software (handle with care)
- 2.1.6. Disable file/ printer sharing
- 2.1.7. Lock PC when away
- 2.2. IoT hardening
- 2.3. Protection against
- 2.3.1. Electromagnetic interference (EMI)
- 2.3.2. Electromagnetic Pulse (EMP)
3. access control
- 3.1. remote access
- 3.2. Service access control (Firewall)
- 3.3. identification
- 3.4. authentication
- 3.4.1. Password-based authentication
- 3.4.2. Biometric authentication
- 3.4.3. Card or Device authentication
- 3.4.4. Digital signature authentication
- 3.5. authorization
4. secured communication
- 4.1. trusted path (tunnel, VPN)
- 4.2. session encryption
- 4.3. mutual authentication
5. resource management
- 5.1. upgradability
- 5.1.1. security updates
- 5.2. resource utilisation
- 5.2.1. least privilege
- 5.3. sec/priv configurability
- 5.3.1. transparency
- 5.4. redundancy
- 5.4.1. continuity
- 5.5. Secure boot
- 5.6. Protection
- 5.6.1. Memory
- 5.6.2. Integrity
- 5.7. Root of trust
- 5.8. Protection against
- 5.8.1. Denial of Service (DoS)
- 5.8.2. Anti-reply
- 5.8.3. Traffic analysis
