Difference between revisions of "IoTSec:Security and Privacy Functionality"
From its-wiki.no
Josef.Noll (Talk | contribs) (→Security, Privacy and Dependability Functionality) |
Josef.Noll (Talk | contribs) |
||
| (16 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
= Security, Privacy and Dependability Functionality = | = Security, Privacy and Dependability Functionality = | ||
| − | + | {{hasKeywords | |
| + | |Keywords=Security, Privacy, Dependability, Security Functionality}} | ||
| + | The starting point for the security listing is the representation of [[System of Systems]] through the [[Multi-Metrics analysis]]. Applications running on the systems typically have functional and non-functional requirements, which also addresses security and privacy requirements. | ||
| − | The | + | The security functionality is available: |
| + | * as [https://webprotege.stanford.edu/#projects/f3ce3328-fe4a-406b-a3ea-7908666c7642 ontology through WebProtege (login required)] in | ||
| + | * [[Media:IoT_SecPrivFunc_LifeMap_v2.pdf|IoT Security and Privacy Functionality Life Map (.pdf)]] | ||
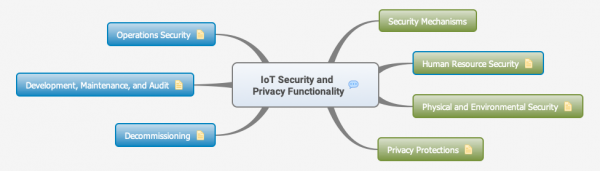
| + | [[File:IoT_Security_and_Privacy_Functionality.png|600px|Security, privacy and dependability functionality (Orig:Owncloud)]]<br/> | ||
| + | Link: owncloud = IoTSec-IKTPluss = IoT_SecPrivFunc_LifeMap_v2.xmind | ||
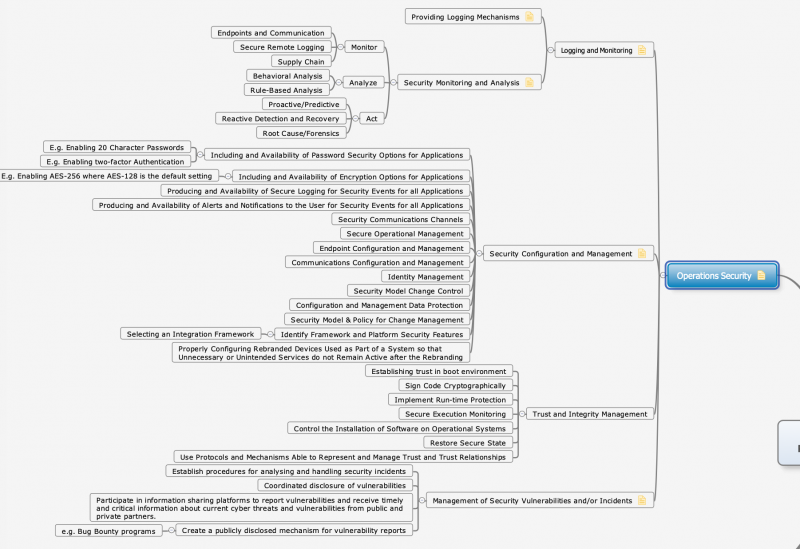
| − | [[File: | + | [[File:Operations_Security.png|800px]] |
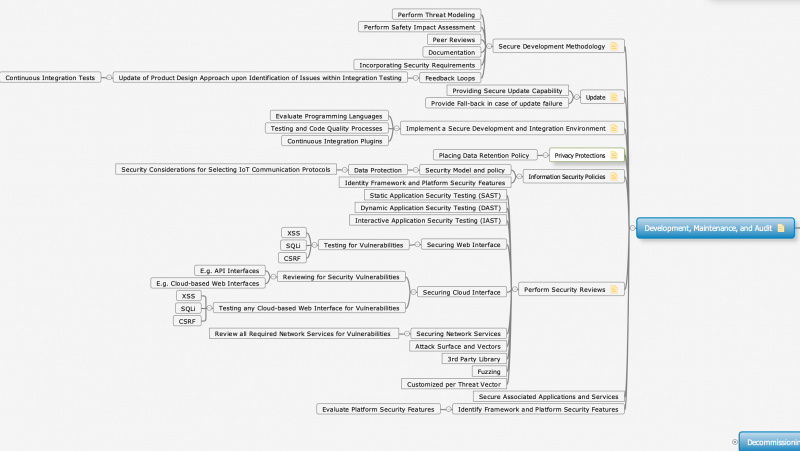
| − | + | [[File:Dev_Maint_Audit_Security.png|800px]] | |
| − | : | + | |
| − | + | ||
| − | + | ||
| − | + | ||
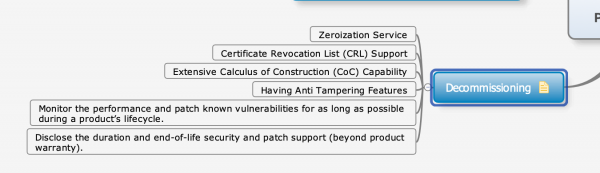
| − | : | + | [[File:Decommissioning_Security.png|600px]] |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
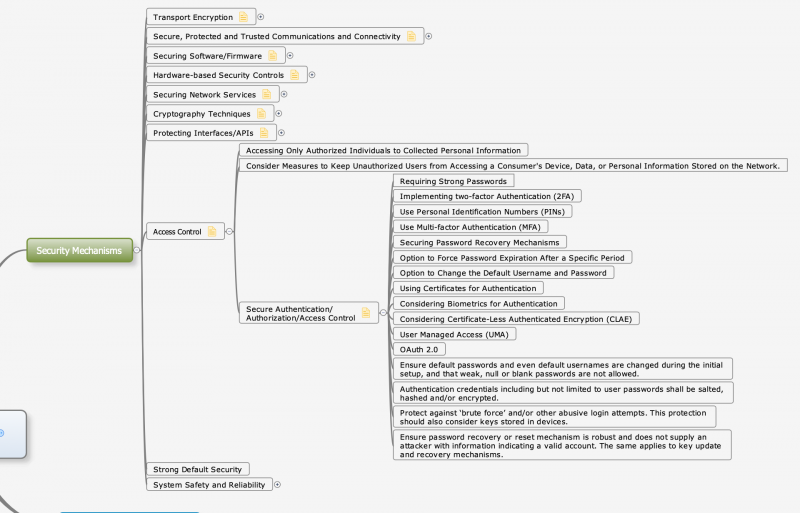
| − | : | + | [[File:Security_Mechanisms.png|800px]] |
| − | + | ||
| − | + | ||
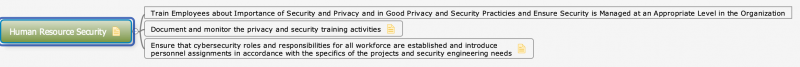
| − | : | + | [[File:Human_Resource_Security.png|800px]] |
| − | + | ||
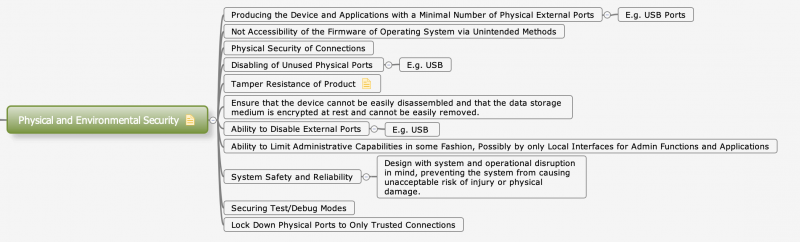
| − | : | + | [[File:Physical_Environmental_Security.png|800px]] |
| − | + | ||
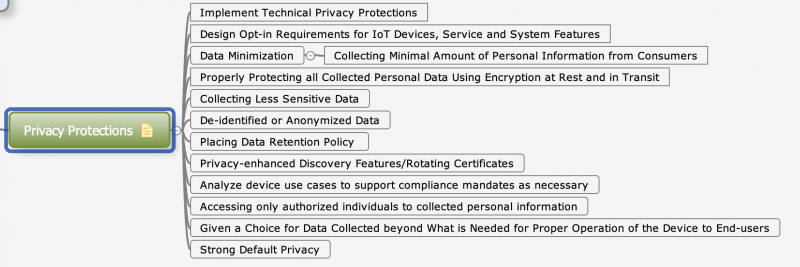
| − | + | [[File:Privacy_Protection.png|800px]] | |
| − | : | + | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | |||
| − | |||
| − | |||
| − | + | == Security and Privacy Functionality paragraphs == | |
| − | : | + | * [[Media:IoT_SecPrivFunc_LifeMap_v2.pdf|IoT Security and Privacy Functionality Life Map (.pdf)]] |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | == Related Standards == | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | * ISO 27000: Overview and Vocabulary (2014) | |
| + | * ''Seraj'' ISO 27001: ISMS Requirements (2013) | ||
| + | * ''Toktam'' ISO 27002: Code of Practice (2013) | ||
| + | * ''Elahe'' ISO 27003: ISMS Implementation Guidance (2010) | ||
| − | + | ||
| − | + | * ''Seraj'' ISO 27004: ISM Measurement (2009) | |
| + | * ''Toktam'' ISO 27005: InfoSec Risk Management (2011) | ||
| + | * ''Elahe'' ISO 27006: Requirements for Bodies Providing Audit and Certification of ISMS (2011) | ||
| − | + | * ''Seraj'' ISO 27007 – 27008: Guidelines for Auditing InfoSec Controls (2011) | |
| − | + | * ''Toktam'' ISO 27014: Governance of InfoSec (2013) | |
| + | * ''Elahe'' ISO 27015: ISM Guidelines for Financial Services (2012) ‐ http://www.iso.org | ||
| − | + | * ISO 31000 - Risk management | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
Latest revision as of 00:39, 6 February 2020
| Security in IoT for Smart Grids | |||||||
|---|---|---|---|---|---|---|---|
|
Security, Privacy and Dependability Functionality
Keywords: Security, Privacy, Dependability, Security Functionality
The starting point for the security listing is the representation of System of Systems through the Multi-Metrics analysis. Applications running on the systems typically have functional and non-functional requirements, which also addresses security and privacy requirements.
The security functionality is available:
- as ontology through WebProtege (login required) in
- IoT Security and Privacy Functionality Life Map (.pdf)
Link: owncloud = IoTSec-IKTPluss = IoT_SecPrivFunc_LifeMap_v2.xmind
Security and Privacy Functionality paragraphs
Related Standards
- ISO 27000: Overview and Vocabulary (2014)
- Seraj ISO 27001: ISMS Requirements (2013)
- Toktam ISO 27002: Code of Practice (2013)
- Elahe ISO 27003: ISMS Implementation Guidance (2010)
- Seraj ISO 27004: ISM Measurement (2009)
- Toktam ISO 27005: InfoSec Risk Management (2011)
- Elahe ISO 27006: Requirements for Bodies Providing Audit and Certification of ISMS (2011)
- Seraj ISO 27007 – 27008: Guidelines for Auditing InfoSec Controls (2011)
- Toktam ISO 27014: Governance of InfoSec (2013)
- Elahe ISO 27015: ISM Guidelines for Financial Services (2012) ‐ http://www.iso.org
- ISO 31000 - Risk management